Law Firms and Cloud Security

Law Firms and Cloud Security: The Guide to Keeping Your Data Secure
Data is priceless. And as a law firm owner, you have an ethical obligation to keep your clients’ information private and secure. Unfortunately, this is increasingly difficult as tech continues to evolve and cybercriminals continue to threaten networks.
Introduction to Law Firms and Cloud Security
According to fresh data, cyber attacks increased by 50% year over year across the board in 2021. In the legal industry, attacks increased by 68% when compared to numbers from the previous year.
Alarming, isn’t it?
For every law firm, it’s no longer a question of if an attack will occur, it’s when. And now is the time to take your data security seriously.
It’s not enough to simply “delegate and forget” when it comes to law firms and cloud security. And it isn’t enough to assume your cloud-based software vendor has all of the necessary security measures in place. Instead, you must take security measures into your own hands.
We know there’s a lot to know about data security. In this guide, we’ll give you a comprehensive overview of the relationship between law firms and cloud security. We break down the best practices you can implement for both cloud-based and premise-based solutions to safeguard your data.
Download the Law Firm Cloud Security Checklist
The ultimate checklist for law firms and cloud security. Included in the checklist:
- What to require of of your cloud software provider
- What to require of your private cloud provider
- How to keep documents & email secure
- How to keep local devices secure
20 Best Practices for Law Firms and Data Security to Implement Today
The scary stats out there are enough to awaken your fight or flight response. Should you step away from the cloud and move to on-premise only? Should you move from on-premise to the cloud? Which is the best option? It’s confusing, to say the least.
Cloud-based solutions are, in many ways, more secure than on-premise software and IT. However, it all depends on your security setup. Here, we’ve compiled a list of 20 best practices for law firms and cloud security that you should consider implementing within your law firm today, regardless of your infrastructure.
1.
Understand Your Legal Obligations
As a lawyer, you know the importance of understanding legal obligations. The same is true for understanding your obligations when it comes to data security. Various laws exist that any attorney should be aware of.
The US has yet to enact principle data protection laws. However, there are many federal and state-level laws that exist. Some states, such as California, have gone above and beyond typical state law to provide enhanced data protection.

For example, California’s Consumer Protection Act (CCPA) is a requirement for those who deal with the personal data of California residents.
Another key law to understand is the EU’s General Data Protection Regulation or GDPR. The GDPR outlines strict guidelines for the protection of the personal information of those living within the EU. Any business or organization that collects or processes data from anyone within the EU must comply.
You must do your research to ensure you comply with the regulations that apply to your firm.
2.
Choose a Well-Recognized Provider
Whether you’re just now building your tech infrastructure or making critical updates, selecting well-recognized providers is key. Some cloud-based software providers are new startups and others don’t have niche experience with law firm data security. You can’t afford to take a gamble here (even if the price is lower).
Law firms and cloud security is something every provider of software or cloud services should prioritize. You should ensure you choose a legal software company that is well-recognized in the industry, be it for private cloud hosting, cloud storage or cloud-based software. This includes recognition from organizations such as:
- The American Bar Association
- Your local State Bar
- Business Publications and Communities
- Partnerships and Integrations with Other Reputable Software Companies
3.
Implement End-to-End Data Encryption
Implementing end-to-end data encryption prevents an outsider from accessing your law firm data while it’s in storage or being transferred between systems or devices.
At Rest
The first part of end-to-end encryption is at-rest encryption. This refers to encryption of the data that is being stored within the cloud or on-premise servers. Stored data can include everything from your CRM to sensitive client documents stored within your filing system.
In Transit
In-transit encryption refers to encrypting the data that is being transferred from one system to another. In many cases, cloud providers will make your cloud accessible to you via a relational database service (RDS) or another remote access technology. These connections must be encrypted using 256-bit encryption to prevent security holes.
Case Study: LexWorkplace
By way of example, LexWorkplace is cloud storage and document management software for law firms. LexWorkplace keeps all data stored encrypted with military-grade encryption, both in-transit and at-rest, automatically when saved to the system.
4.
Deploy End-to-End Virus Protection
When it comes to law firms and cloud security, there’s more to consider than just the security of your chosen software platform.
End-to-end virus protection should be a priority. Malware and other viruses can lead to serious consequences such as critical network downtime and data loss. To combat viruses, you must deploy high-quality antivirus software. However, you shouldn’t stop there.
For end-to-end protection, you should choose a software or cloud provider that will actively monitor and update your virus protection on each of your servers. In addition, the provider should monitor and update virus protection on each of your desktop and laptop computers as well as other devices.

Real-time monitoring will ensure any intrusion or malicious activity is stopped in its tracks before it ever takes hold of your system. While some platforms will promise to alert you when potential malicious activity is detected, these tools are no substitute for human intervention.
5.
Block Ransomware
Many cybercriminals have discovered that holding data or systems for ransom is a simple and effective way to make some cash. After all, businesses will typically do whatever it takes to get their data back.
It’s a common misconception that antivirus software will protect systems from ransomware. However, ransomware is unique and often missed by antivirus software. That’s why it’s important to deploy ransomware-specific protection software to identify and block these malicious attacks.
6.
Add Enterprise Firewall Protection
Like virus protection, keeping your local networks and devices safe is a key element of law firms and cloud security.
A firewall’s purpose is to monitor network traffic and block suspicious or unauthorized activity. The firewall works based on a set of predefined rules and can prevent a wide range of malicious activity such as viruses, worms, and denial of service (DoS) attacks.
While it’s true that virtually every network features a basic firewall, that isn’t enough when it comes to law firm data security. We recommend upgrading your firewall to an enterprise-grade system for the best protection.

Enterprise firewall systems include additional tools such as active threat detection, regular security updates, complex traffic monitoring, full network traffic visibility, and more.
7.
Activate “Active” Threat Monitoring
While security tools such as firewalls and antivirus software are perfect for passive protection, data security requires active protection too. Threat monitoring refers to the process of monitoring networks and security data for potential threats. If a potential threat is found, incident response can begin immediately.
Threats can take months to detect. And by the time they’re detected, the damage is already done. Active threat monitoring can reduce detection time, potentially saving you from costly downtime and severe data loss.
Many IT providers and software vendors include active threat monitoring as part of their services. Using various IT tools and people power, these services actively watch for threats such as viruses, failed login attempts, security exploits, and more.
8.
Regular Server & Software Patching
A critical part of threat prevention is ensuring your servers are updated with the latest security patches often. Security patches are meant to resolve server issues, fix server errors, and provide critical updates. Patches will eliminate potential vulnerabilities within your operating system, software, third-party libraries, and beyond.
When it comes to cloud-based software for law firms, it’s important that your software vendor regularly patches their servers and any third-party libraries they use. (Libraries are typically open source pieces of software that software companies leverage to avoid having to reinvent the wheel.)
9.
Segregate Tenants
Data segregation enables you to set access rules for specific sets of data or user groups. This ensures only authorized users have access to specific data. Plus, segregation helps minimize cyberattacks. Should a criminal gain access, they won’t be able to access your entire network at once.
Segregation can occur on both private servers and cloud-based software. For example, for private servers, each firm (each tenant) must be segregated using active directories and network-level segregation (also known as dedicated subnets).
For cloud-based software, tenants should be segregated at the back-end level via user authentication and software code.
10.
Understand Your Software Company’s Subpoena Policy
As a lawyer, you’re no stranger to the subpoena. However, your cloud-based software company might be. Data is often subpoenaed for various court cases and it’s your right to be notified when a subpoena is received by your provider.
Whether you’re selecting a new provider or already have one, it’s critical to know the process they’ll follow if they receive a subpoena for data. Ensure they have a process in place to notify you first before any action is taken.

Ideally, your cloud software provider should have fully-installed policy of notifying you in the event they are served with a subpoena regarding your data, and give you all allowed time to respond before providing data to any third party.
11.
Implement Multi-Factor Authentication (MFA)
If there’s one thing on this list you can implement within your firm almost immediately, it’s multi-factor authentication or MFA. Multi-factor authentication requires users to provide two (two-factor authentication or TFA) or more verification factors before they gain access to any of your systems or data.
In a time when passwords are easily compromised, MFA provides tight protection against threats. MFA can be completed using various verification factors. For example, users can enter a username and password, and then use a tool such as Google Authenticator to finish the process via mobile device.
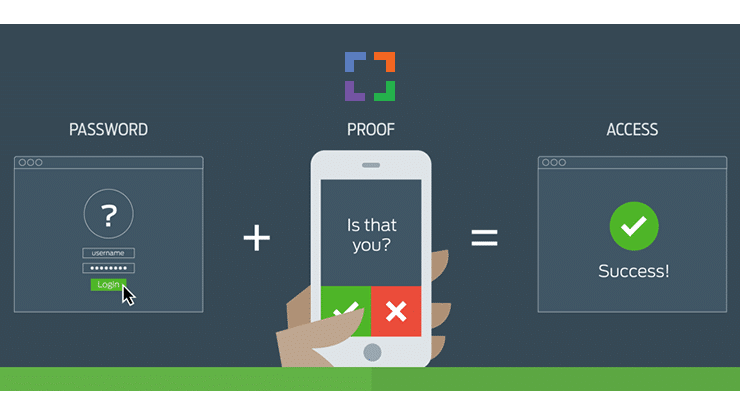
Another example is the one-time password (OTP). Before gaining access, users can receive an OTP on their device that they will then use to log into the system. MFA prevents cybercriminals from gaining access, even if they manage to guess a user’s password.
Case Study: LexWorkplace
By way of example, LexWorkplace includes native MFA. You can require that every login to your LexWorkplace account, and all of the files and documents you store in it, be authenticated with an MFA app.
12.
Adopt a Security Framework
Data security is a complex process. Luckily, many organizations have perfected data security and are willing to share their expertise. Security frameworks such as the Cybersecurity Framework (CSF) by the NIST provide detailed guidance on the steps you must take to protect your data.
The CSF focuses on five key functions—Identify, Protect, Detect, Respond, and Recover. And for each function, the CSF provides best practices to follow.
There are plenty of other frameworks to choose from as well, including the HITRUST Cybersecurity Framework, Control Objectives for Information Technology (COBIT), and more. Choose a framework that fits your current comfort level and data security needs.
13.
Ensure Ownership of Your Data
We know you know this, but for the sake of this guide: Read the contract. This is especially true when storing data in the cloud. You’ll want to ensure that your data stays your data—forever.

The service contract shouldn’t be unambiguous and should give you perpetual ownership of your data, regardless of what happens. There are questions you should ask any cloud software provider before signing on the dotted line:
- Who owns the data once it’s stored in the cloud?
- How will I get my data back if we change providers?
- Who will have access within your company to my data?
- What process do you follow regarding my data in the event of provider change?
This is another reason why we recommend finding a provider that’s used to working with law firms and their ethical obligations.
14.
Ensure Physical Safeguards of Data
Physical protection of your provider’s data centers is just as important as data protection. Your software provider should have strong safeguards in place such as strict, documented physical access requirements for those entering the data center.
Other safeguards include 24/7 monitoring of the data center, disaster mitigation systems (such as fire protection systems), and simple safeguards such as locked access doors and security cameras.
15.
Ensure Data Sovereignty
Data sovereignty refers to what governmental authority may have implicit or explicit “rights” to your data. This is critical as every state bar will agree that all client data should be stored within the continental US, including your cloud-based backups.

You’ll want to ensure that your provider is storing your data in a data center that’s within the US. This ensures data sovereignty, which means following the laws that apply to the country your data resides in. For example, data stored within the US must follow US data laws.
For law firms, sovereignty is critical. If your data is stored in a country outside of US jurisdiction, there are plenty of potential ethical consequences.
16.
Encrypt and Secure All Communications
A ton of work happens via email and other communication tools such as Slack, especially in today’s remote work environment.
Consider how many client communications you have via email and how much confidential information you share via chat tools. Encryption helps protect this information from falling into the wrong hands.
In the past, emails were easily intercepted in transit. However, most email providers now use transport layer security (TLS) encryption to prevent interception by cybercriminals.
This isn’t exactly enough. Instead, you should opt for end-to-end encryption to protect your data even when it’s sitting in your inbox. In this process, you encrypt a message before it is sent and the recipient decrypts the message once received.
There are many email encryption solutions available out there. Many of them are policy-based which means the system will decide which emails are sensitive and encrypt them automatically.

Chat
Chat tools offer law firms a simple way to communicate with team members and colleagues throughout the day. However, they’re not all created equal. You should opt for chat tools that feature end-to-end encryption such as Slack and Microsoft Teams.
17.
Develop Company Data Security Policies and Training
Your legal team is the first line of defense when it comes to mitigating security threats. That’s why all members of your team must understand the importance of threat prevention and what to do in the event of a breach.
You should develop a company data security policy that includes all of your procedures and requirements. For example, you’ll want to include password requirements, your bring-your-own-device (BYOD) policies, internet usage policies, social media usage policies, and incident reporting and mitigation steps.
You’ll also want to implement periodic employee training to ensure everyone is up to speed on best practices. For example, your employees should know what a spam email looks like, how to create proper passwords, and how to use multi-factor authentication.
18.
Implement Permission and Access Control
Access control refers to restricting and enabling access to data sources based on user permissions. Both permissions and access control can reduce the chances of sensitive data falling into the wrong hands. Access control should be enabled at the system level and the software level for the best results.
There are two common methods for access control, including Least Privilege and Need to Know. Through Least Privilege, users can only use data in ways that pertain to their job duties. And through Need to Know, users can only see the data they need to complete their critical tasks.
Both of these methods should be implemented for the best results. Access and permissions should also be monitored often to ensure access is appropriate.
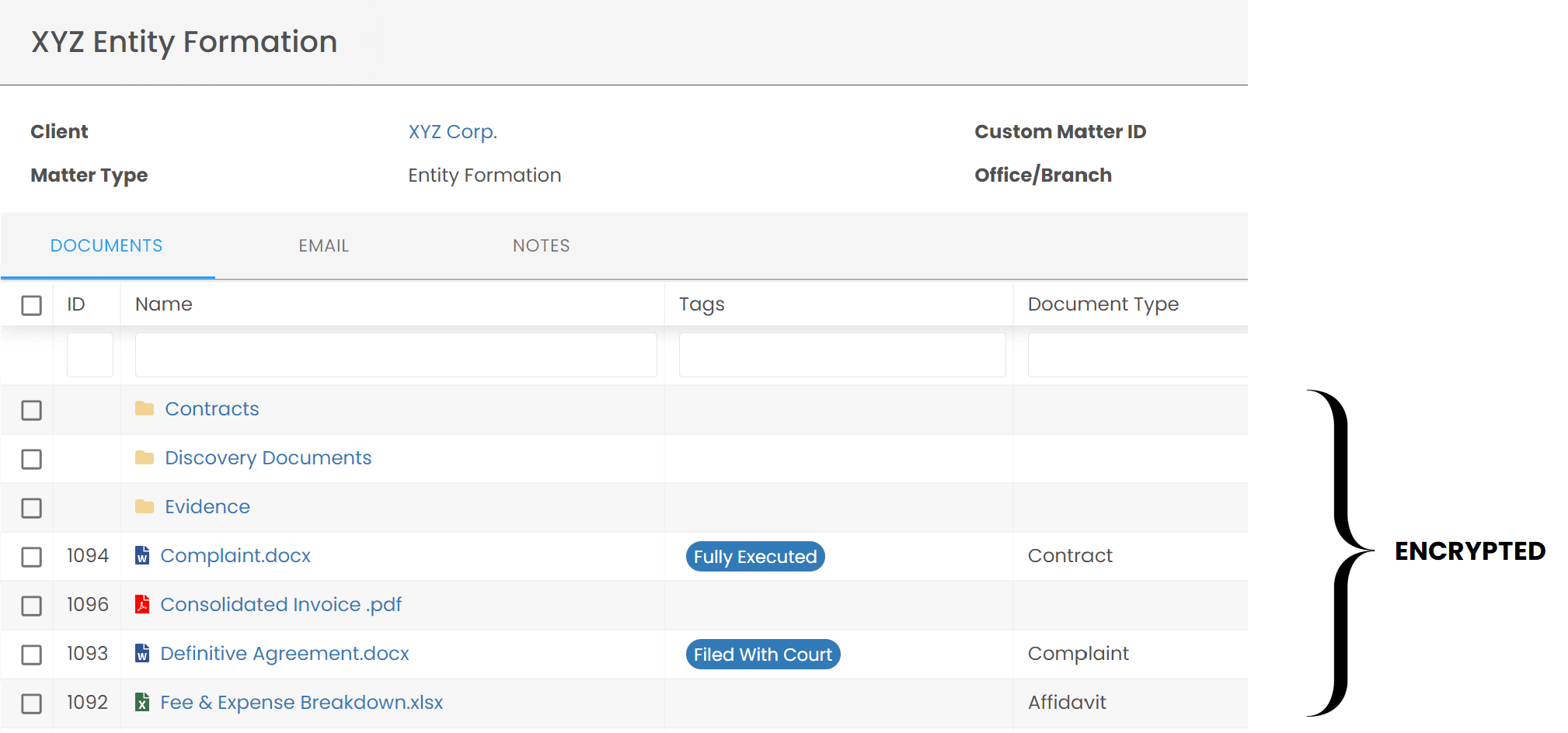
Case Study: LexWorkplace
>By way of example, LexWorkplace allows you to manage permissions at the Matter level. In LexWorkplace, each matter serves as a virtual file cabinet that can hold documents, files, email and notes for that matter. And–you can limit access to any matter to specific people or groups within your firm.

19.
Perform Regular Security Reviews
Data security is far from a one-and-done thing. Data advances daily and so do the threats against it. Make sure you’re performing regular security reviews to spot weaknesses and risks.
For example, you’ll want to ensure permissions are appropriate, employees are using MFA correctly, firewalls are working as they should, and more.
You should also take the time to periodically update your data security policies and ensure all employees (both tenured and new) have easy access to updated copies.
20.
Develop an Incident Response Plan
While following the above 19 best practices is the best way to prevent a security incident, nothing is completely foolproof. That’s why it’s best to prepare now, just in case.
Start by developing an incident response plan. You can do so by answering these questions:
- Who will be on your incident response team?
- What steps will you and your team members take to contain a security event?
- What is your business continuity plan? In other words, what happens to ensure your business can continue after a breach?
- Which steps will your IT provider take?
- Who should be contacted in the event of a breach?
Once you develop your plan, you’ll want to test it to ensure it works as it should. We recommend doing this often. Testing your plan helps you see where updates should be made. Plus, it’s good practice for your team too.
Download the Law Firm Cloud Security Checklist

Ready to up your law firm data security? We’ve got you covered in this simple checklist. Included:
- What to require of of your cloud software provider
- What to require of your private cloud provider
- How to keep documents & email secure
- How to keep local devices secure
5 Must-Have Tools to Make Your Law Firm More Secure
While improving your data security can be a challenging process, there are plenty of tech tools out there to help. Here is a small collection of some of our favorites you can get started with today.

Duo Security
Duo is a security platform that helps organizations of all sizes protect their critical data. Duo offers several security features, including the ability to enable MFA, confirm user identities, monitor devices, and enable single sign-on (SSO).
Google Authenticator
Google Authenticator is a tried and true MFA app that generates two-step verification codes on any mobile device. This is a great tool for law firms that utilize Google Workspace or Google accounts for access.

Dropsuite
Dropsuite was built specifically for backing up, restoring, and migrating Microsoft 365 and Google Workspace email accounts. Microsoft 365 backups are especially limited so we recommend Dropsuite for added protection.

LastPass
LastPass is simple password management software. It works by storing and remembering all of your passwords for each site and app you use. It increases security by eliminating the need to write passwords down, and can also generate secure, difficult-to-brute-force passwords as needed.
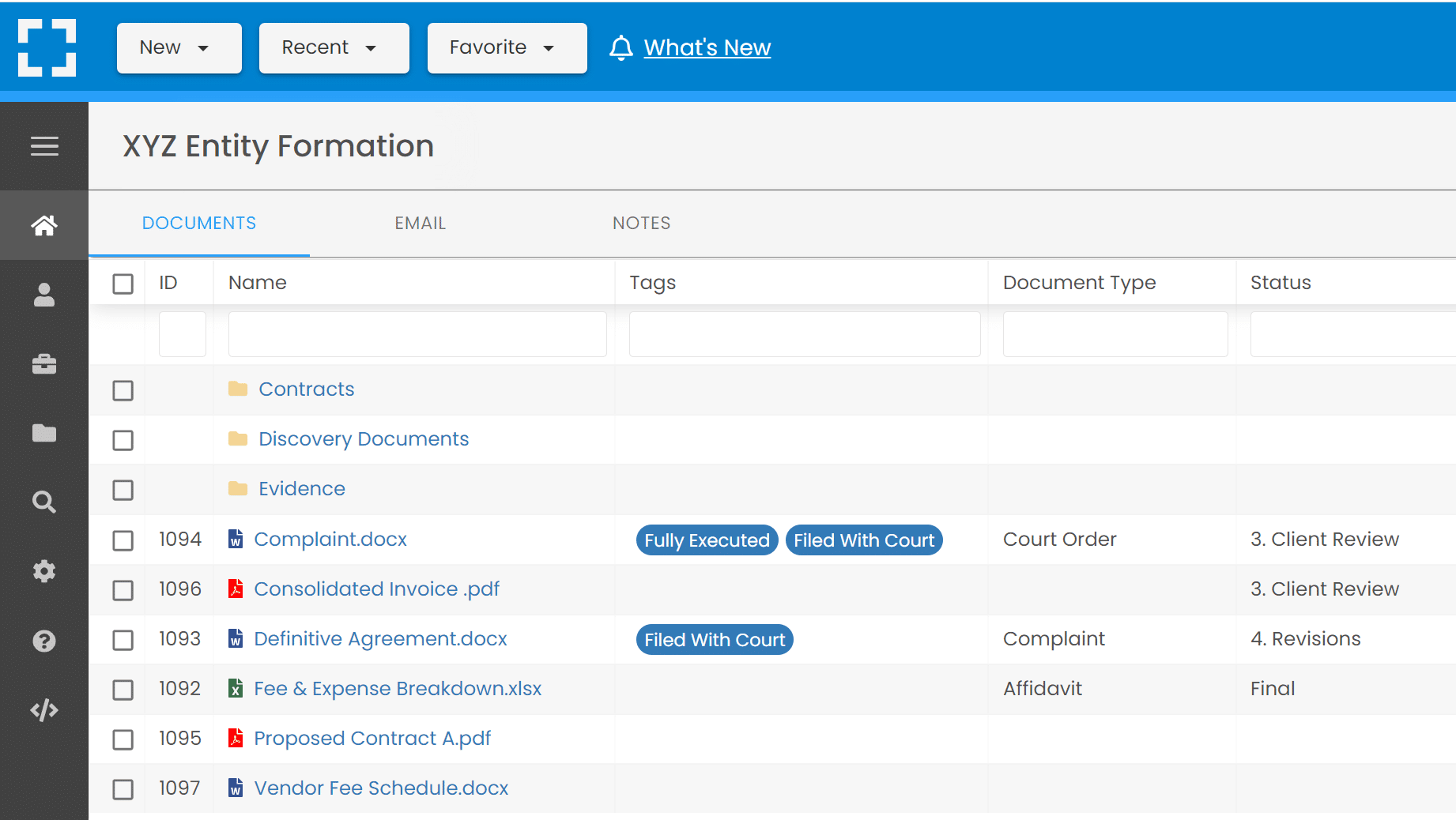
LexWorkplace
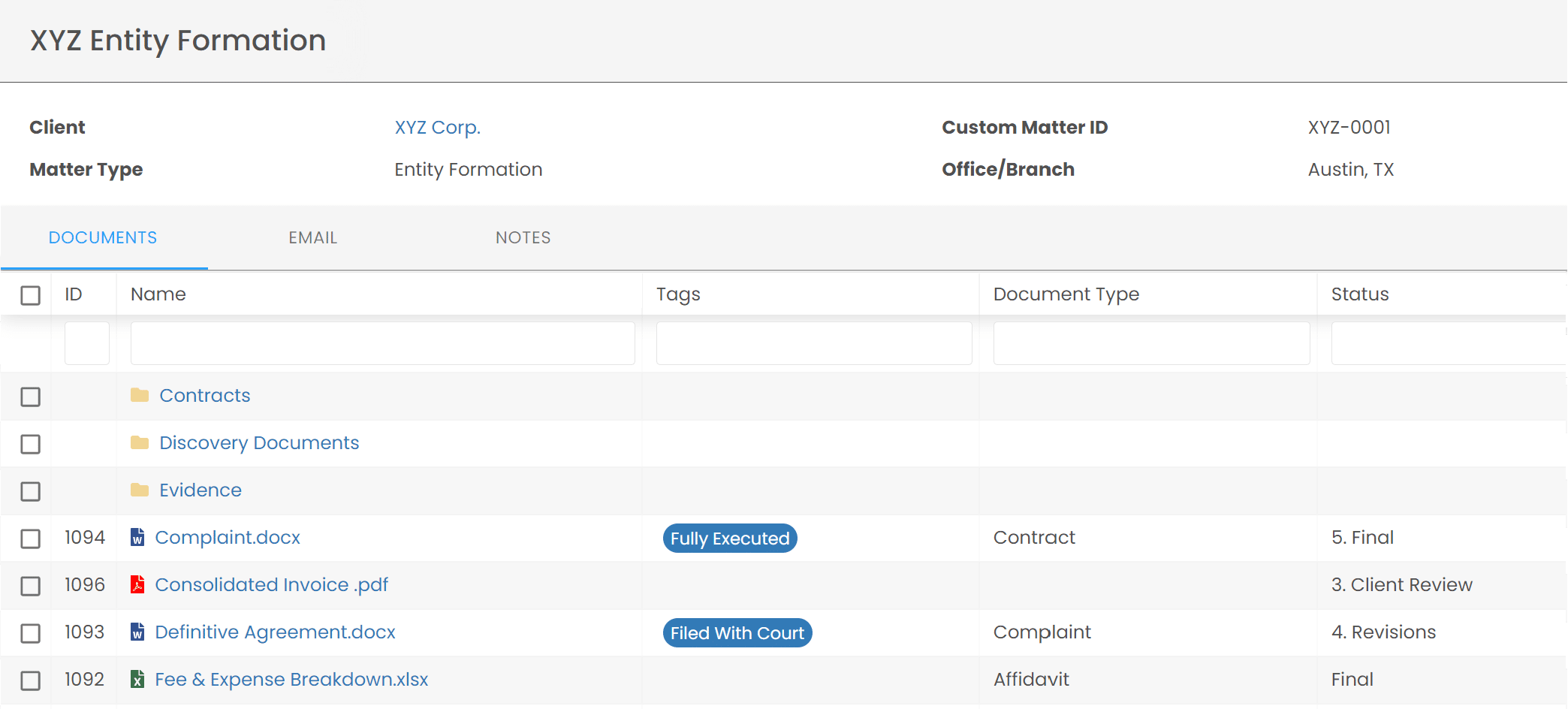
LexWorkplace is a complete document management system (DMS) for law firms. You can safely and securely store all of your documents and emails inside LexWorkplace which includes security features such as:
- End-to-end data encryption
- Geographic redundancy throughout the US
- Multi-factor authentication
- User control, including permissions and defined access
Using LexWorkplace, you can ensure your critical law firm and client data is secure and accessible at all times.
Boost Your Law Firm Data Security With LexWorkplace
LexWorkplace was built for data security and compliance. LexWorkplace not only helps you keep firm docs and matter docs organized, it keeps your data secure with features such as end-to-end data encryption and geographic redundancy.
Looking for Document Management Software?
LexWorkplace:
Modern Document Management for Law Firms
LexWorkplace is document & email management software, born in the cloud and built for law firms. Here’s a quick primer on how it works, or get your free trial to discover LexWorkplace for yourself.
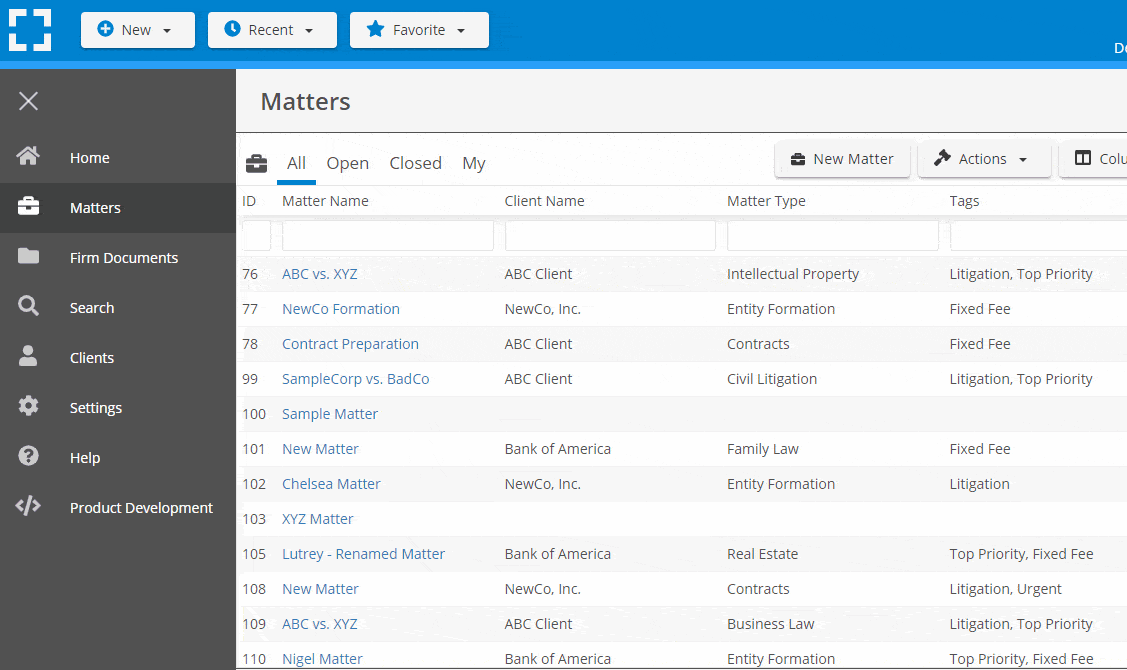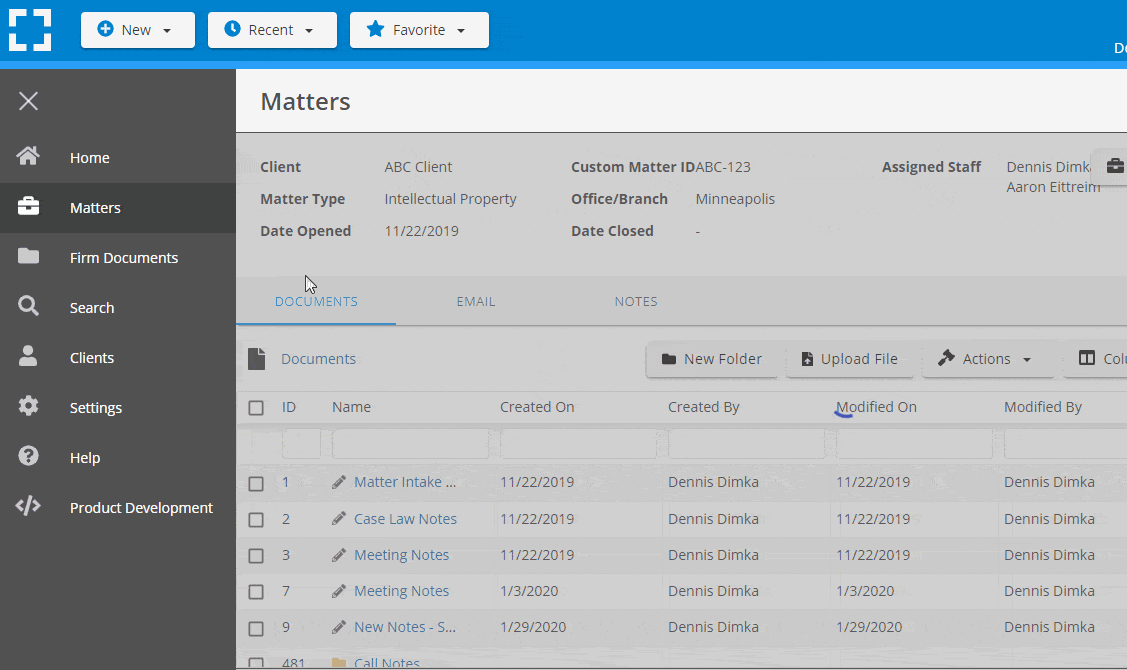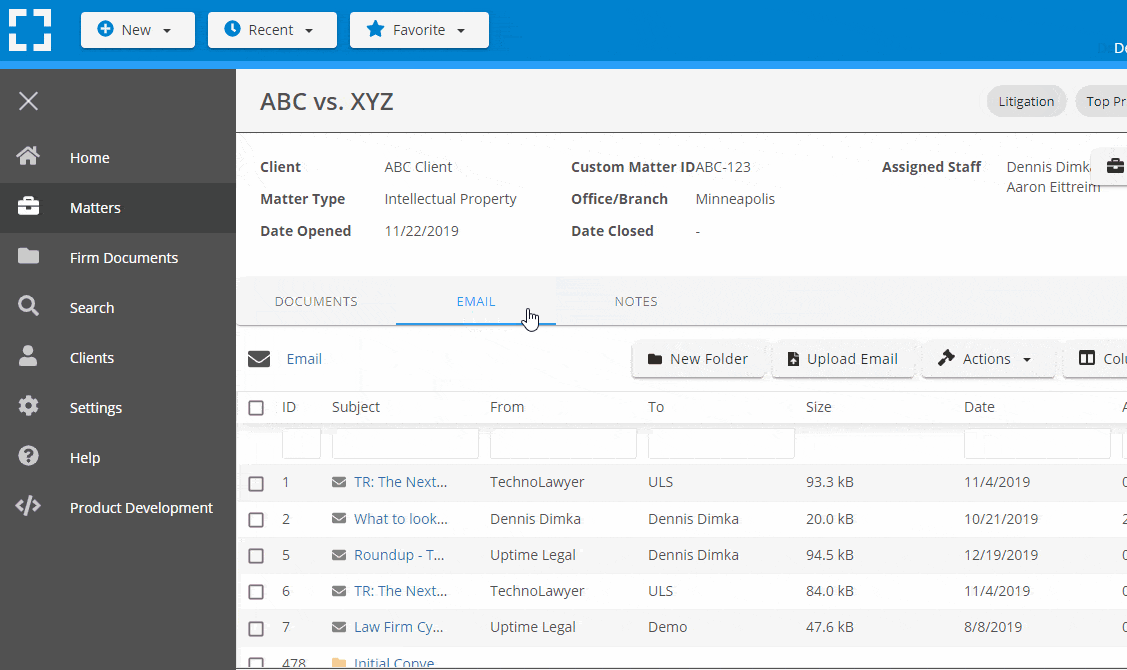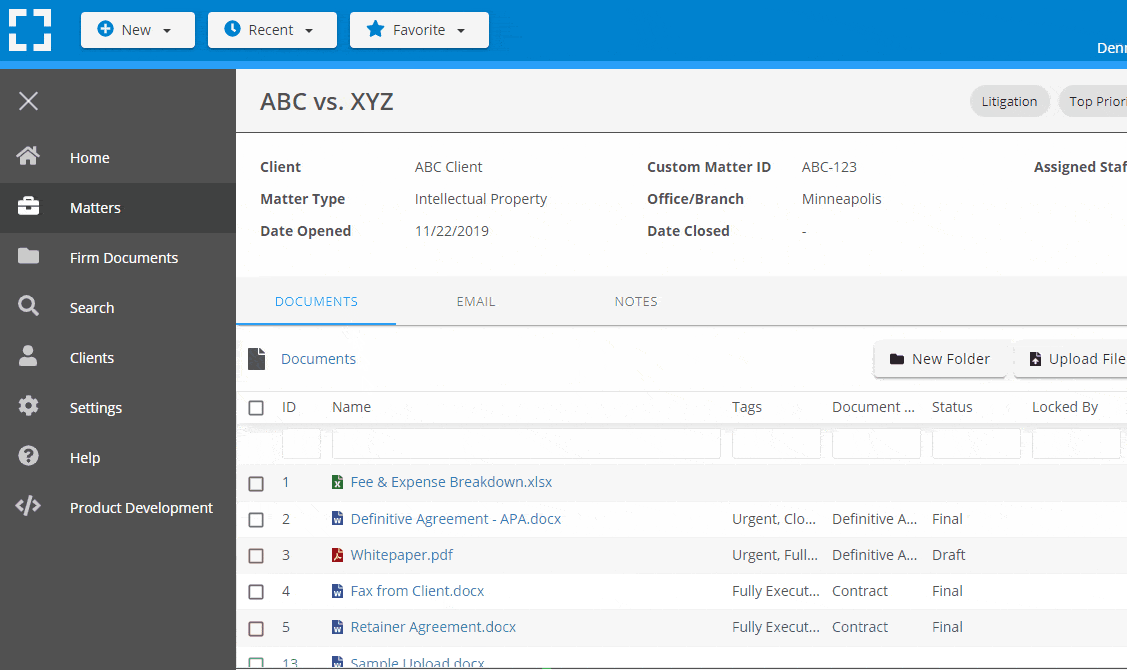
Organize by Client & Matter
Organize documents, email and notes by client or matter. Store and manage all data for a case or project in one place.
Go Beyond Basic Files & Folders
Supercharge your firm’s productivity with true DMS functions.
- Version Management
- Document Tagging & Profiling
- Document Check-Out / Check-In
- Microsoft Office Integration
- Automatic, Integrated OCR
- Convert Word Docs to PDF
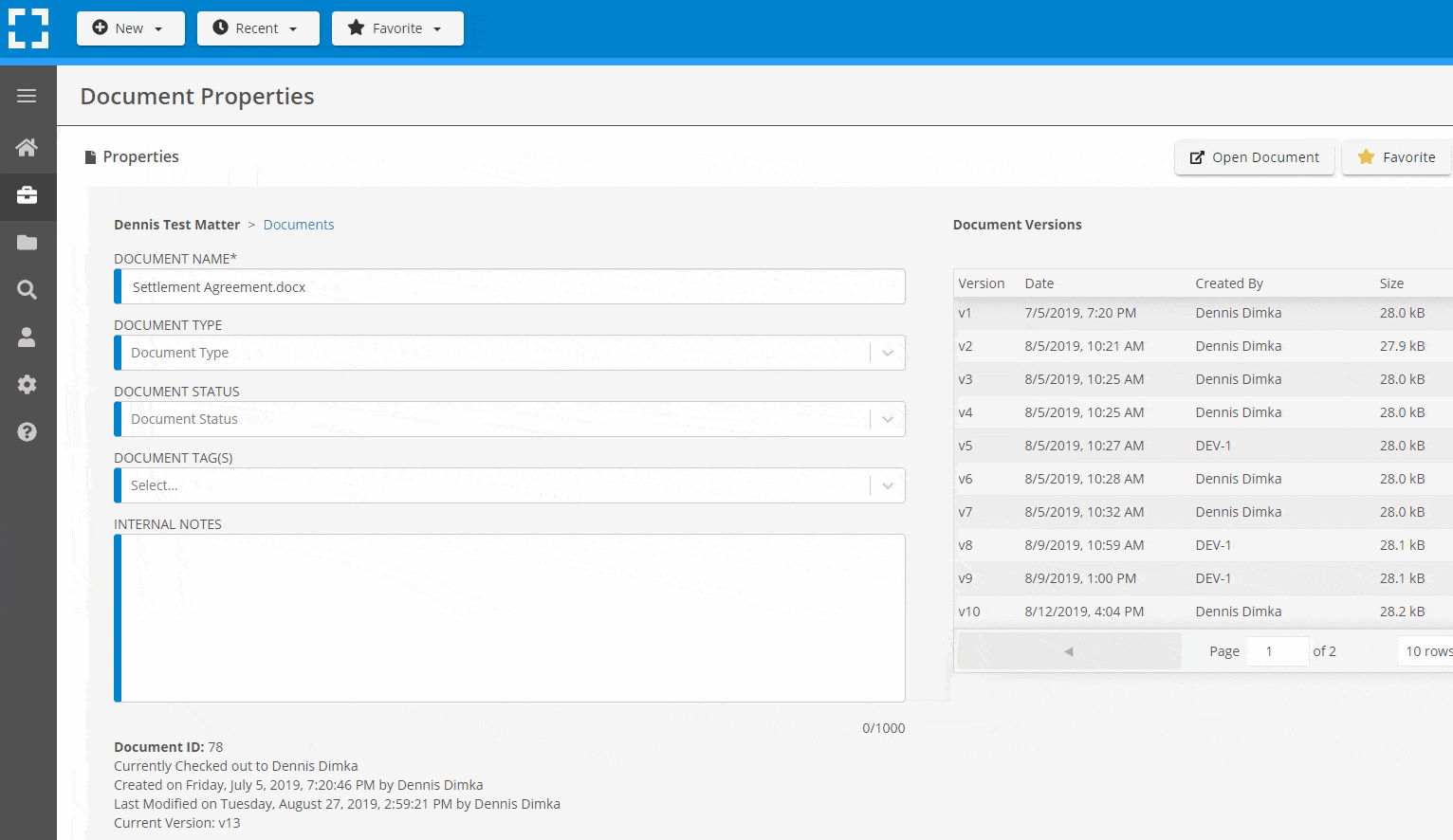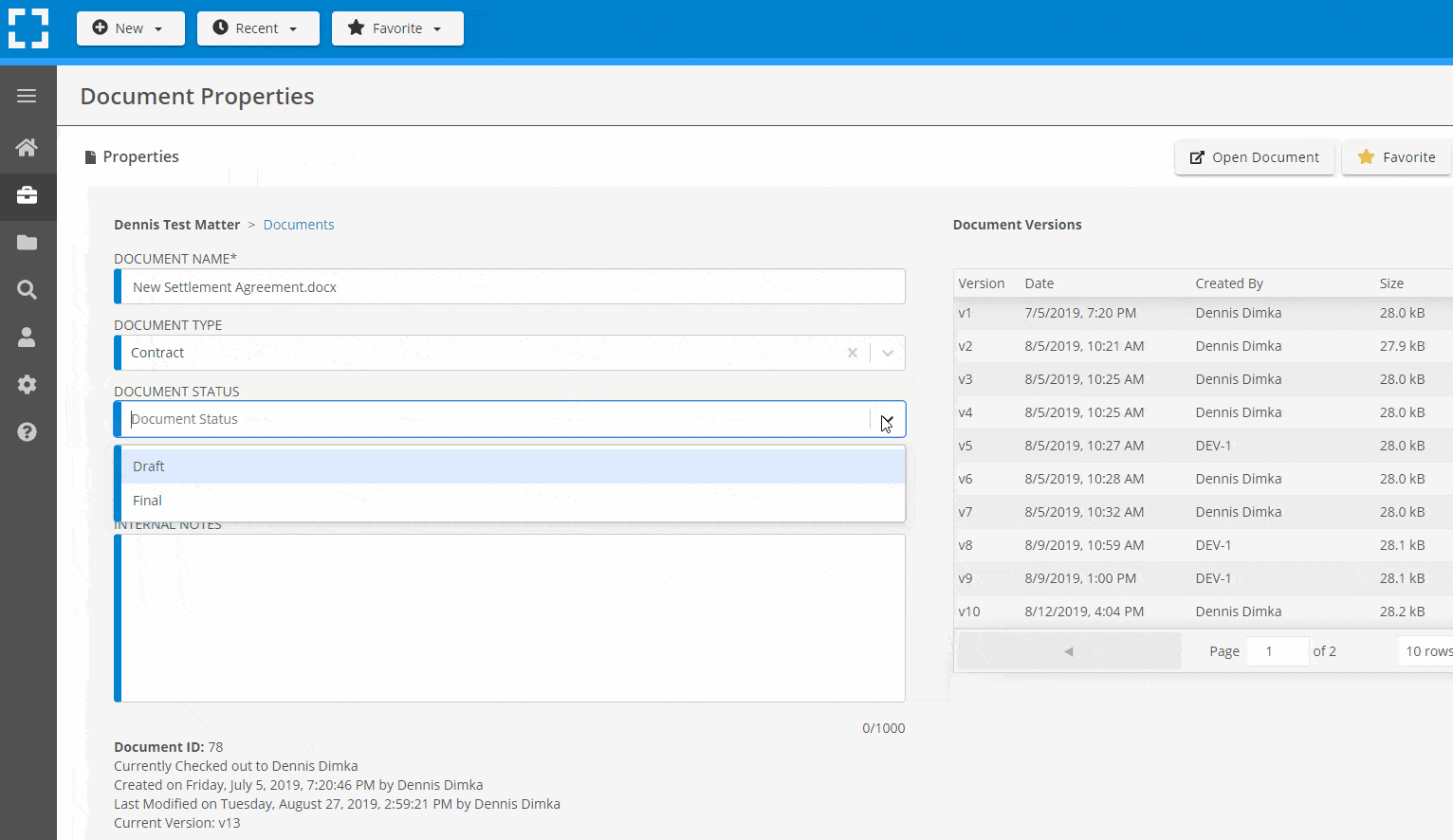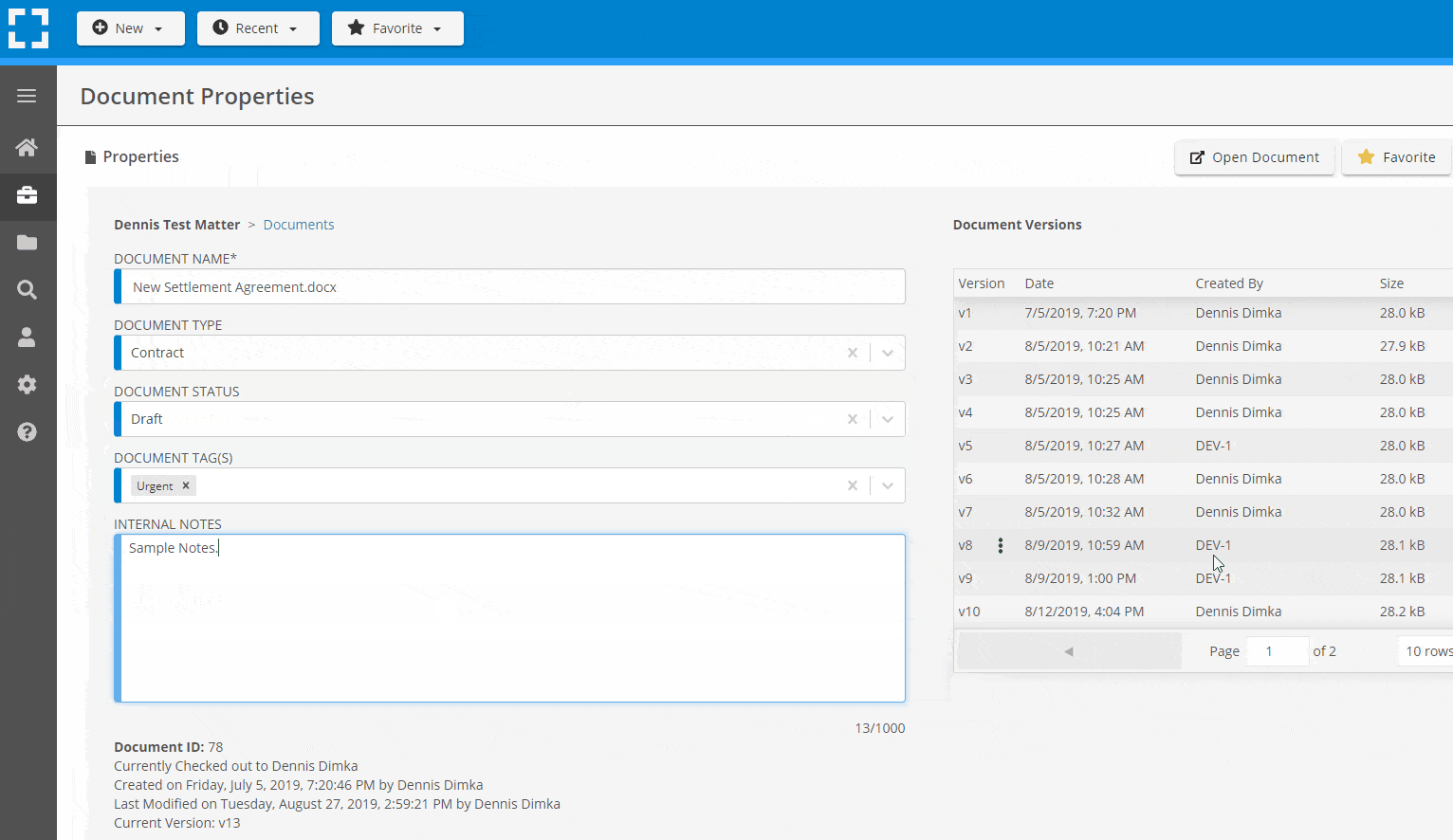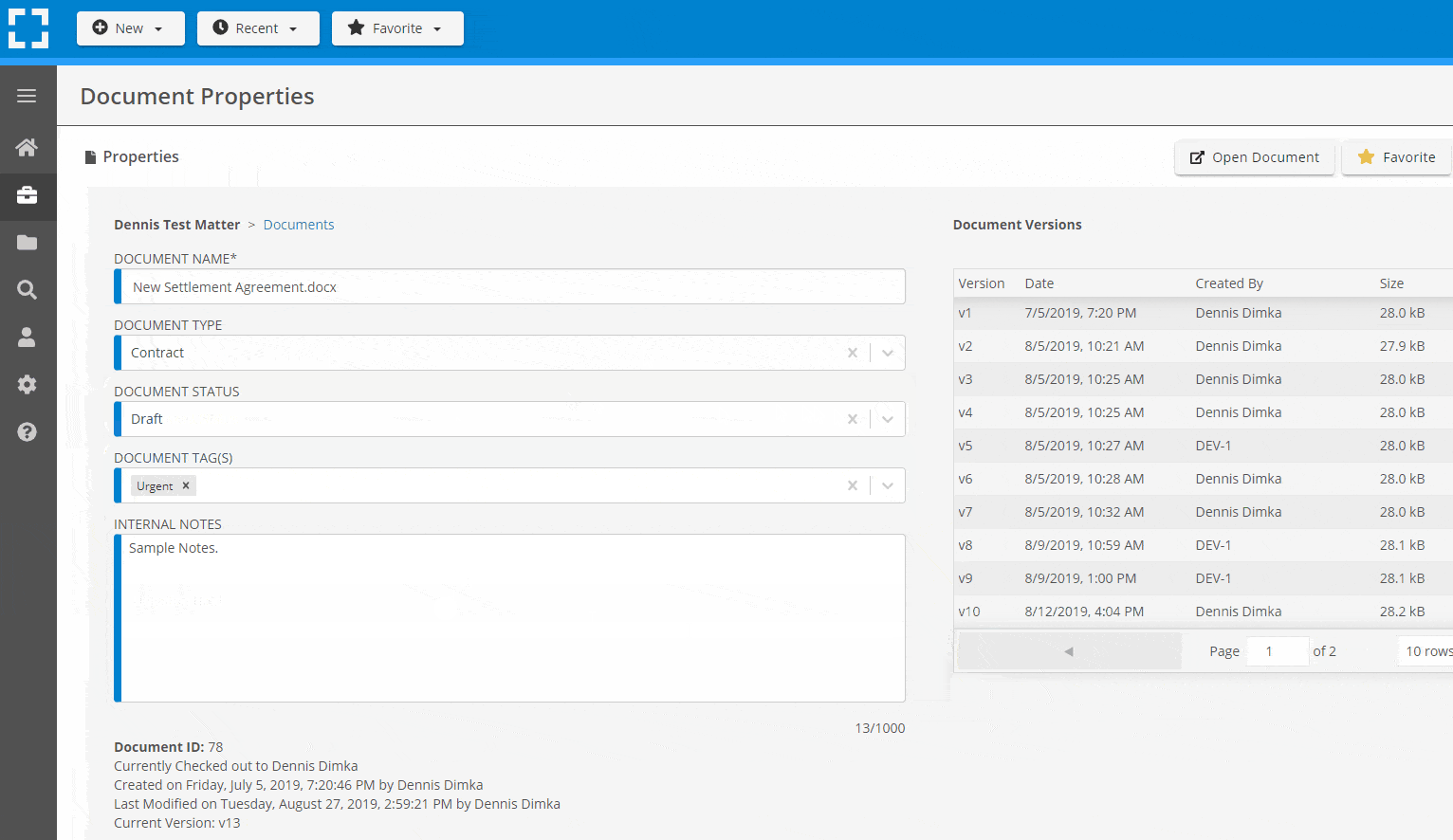
Search Everything
LexWorkplace is like Google for your law firm. Search across millions of pages, documents, folder email and notes in seconds. Refine your search by matter, document type, author and more.
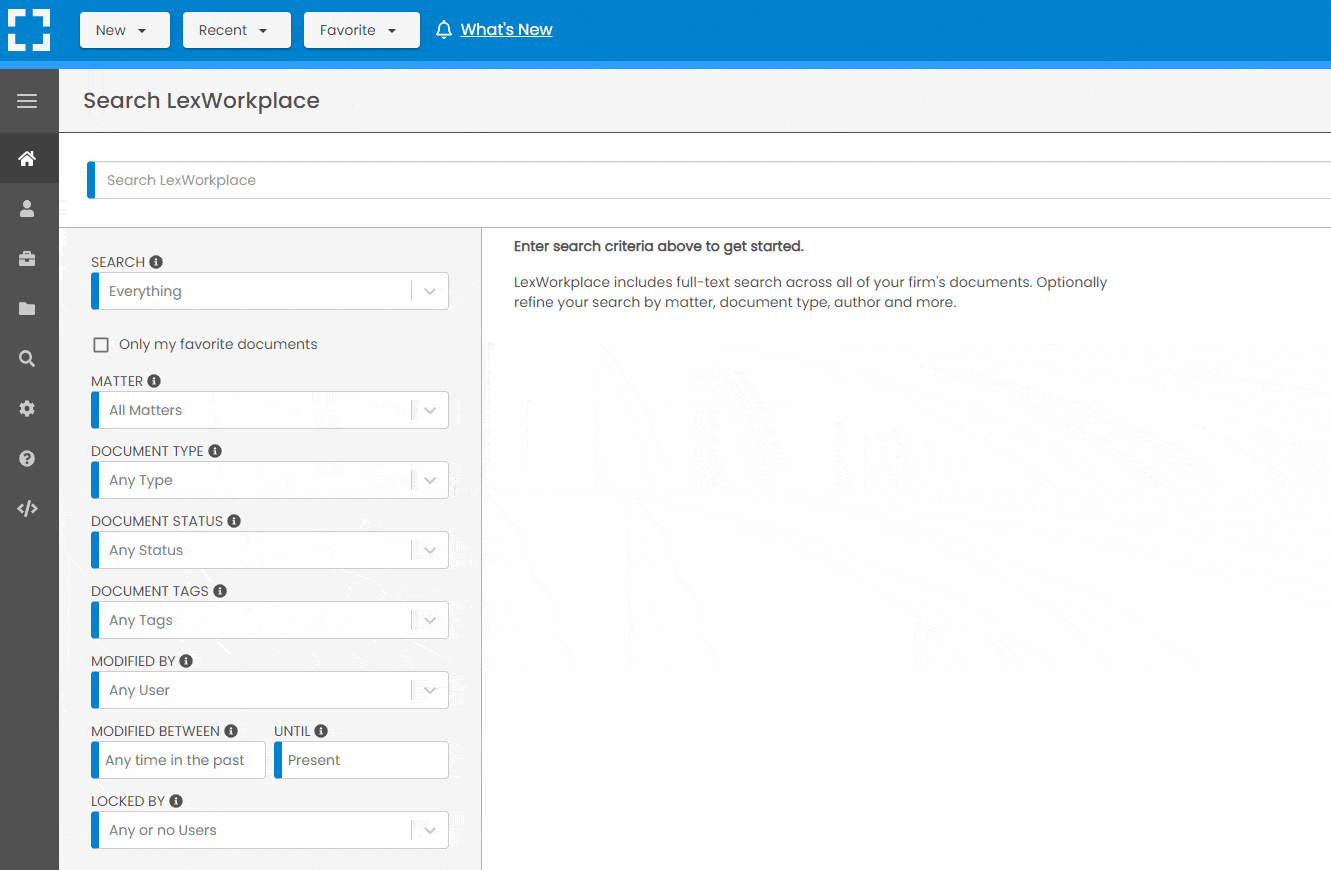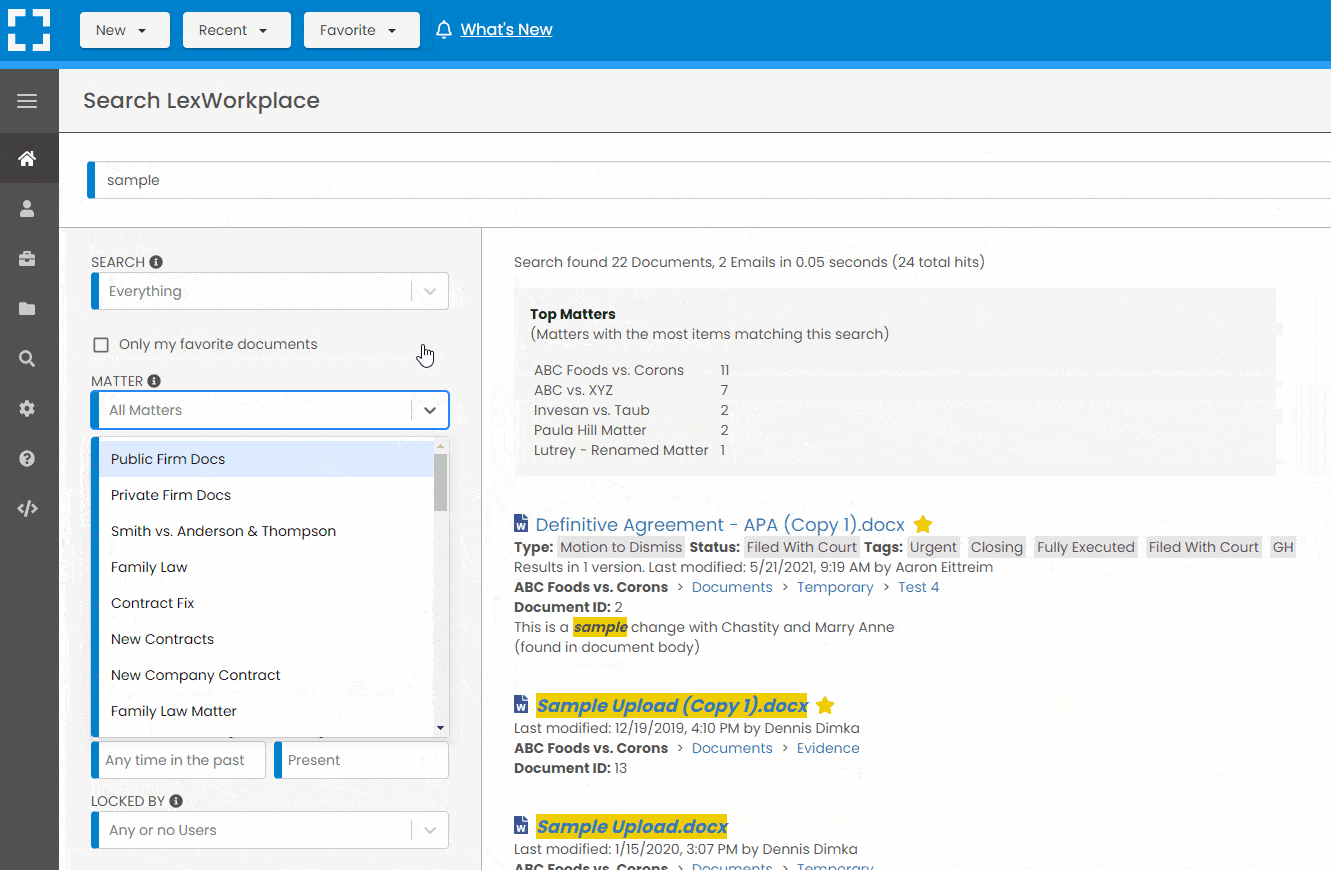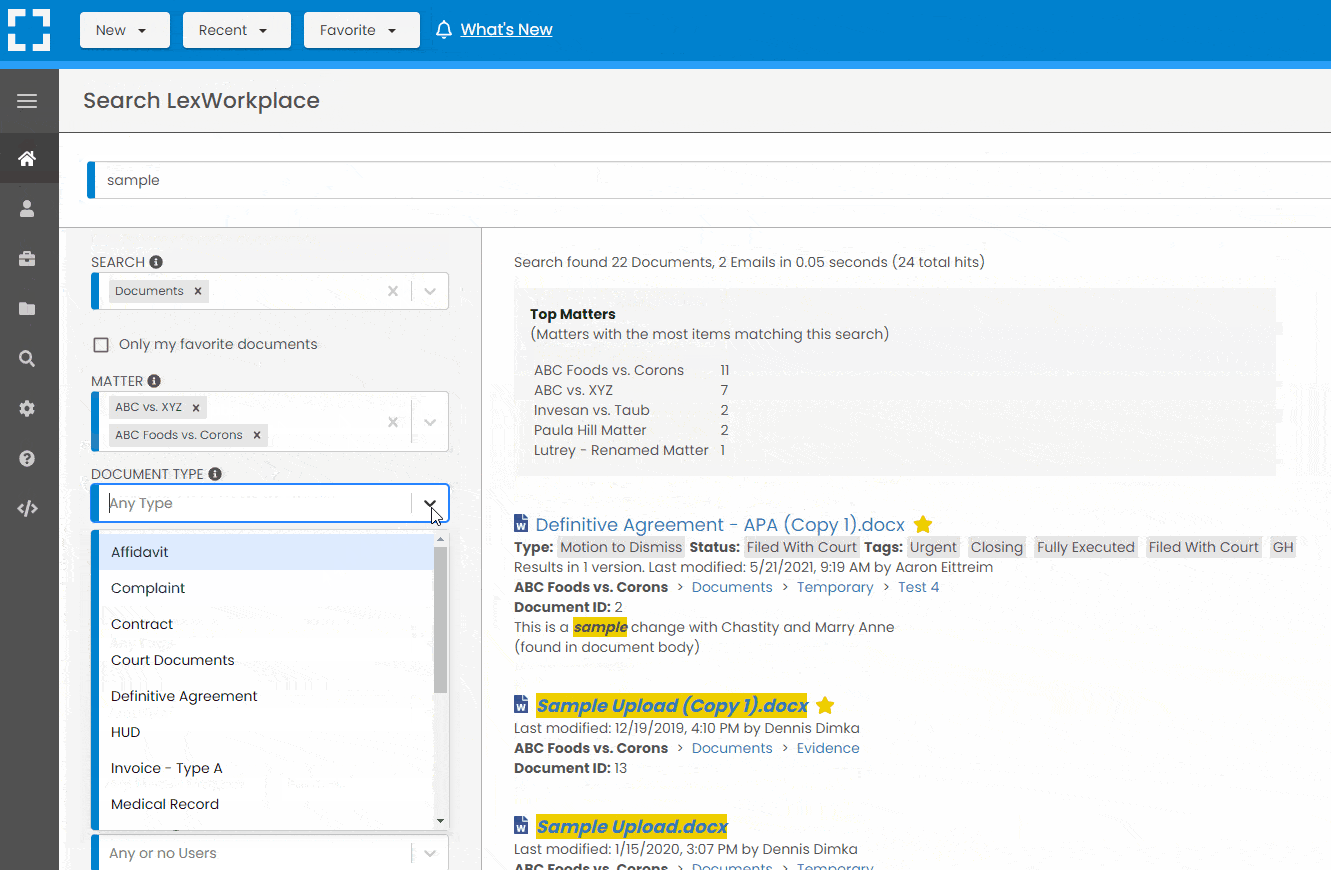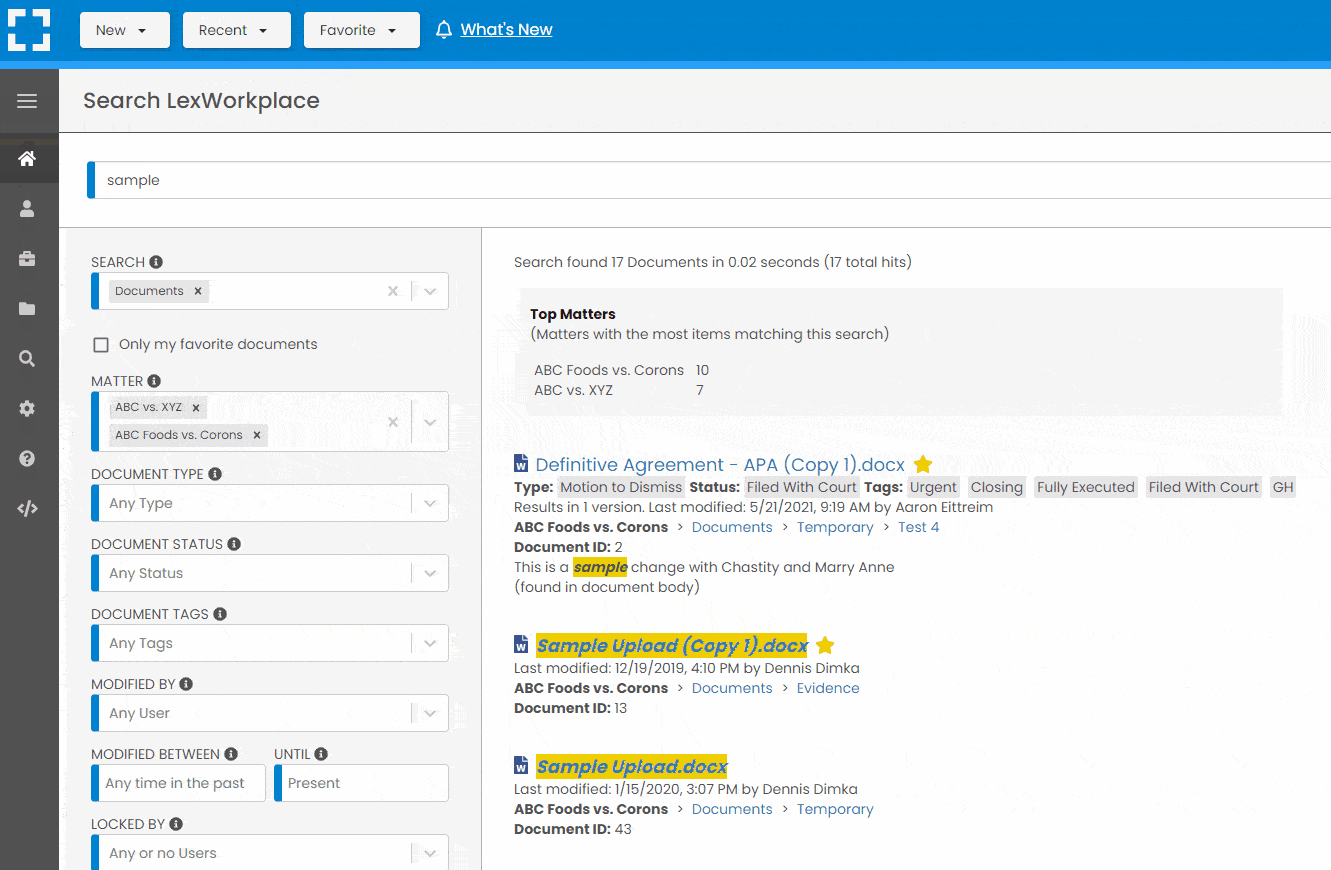
Search by…
- Client or Matter
- Document Type (Contract, Complaint, Order, etc.)
- Document Status (Draft, Final, etc.)
- Document Tags (Filed With Court, Fully Executed, etc.)
Outlook Integration + Comprehensive Email Management
Save emails to a matter without leaving Outlook. Saved emails are accessible to your entire team, organized and searchable.
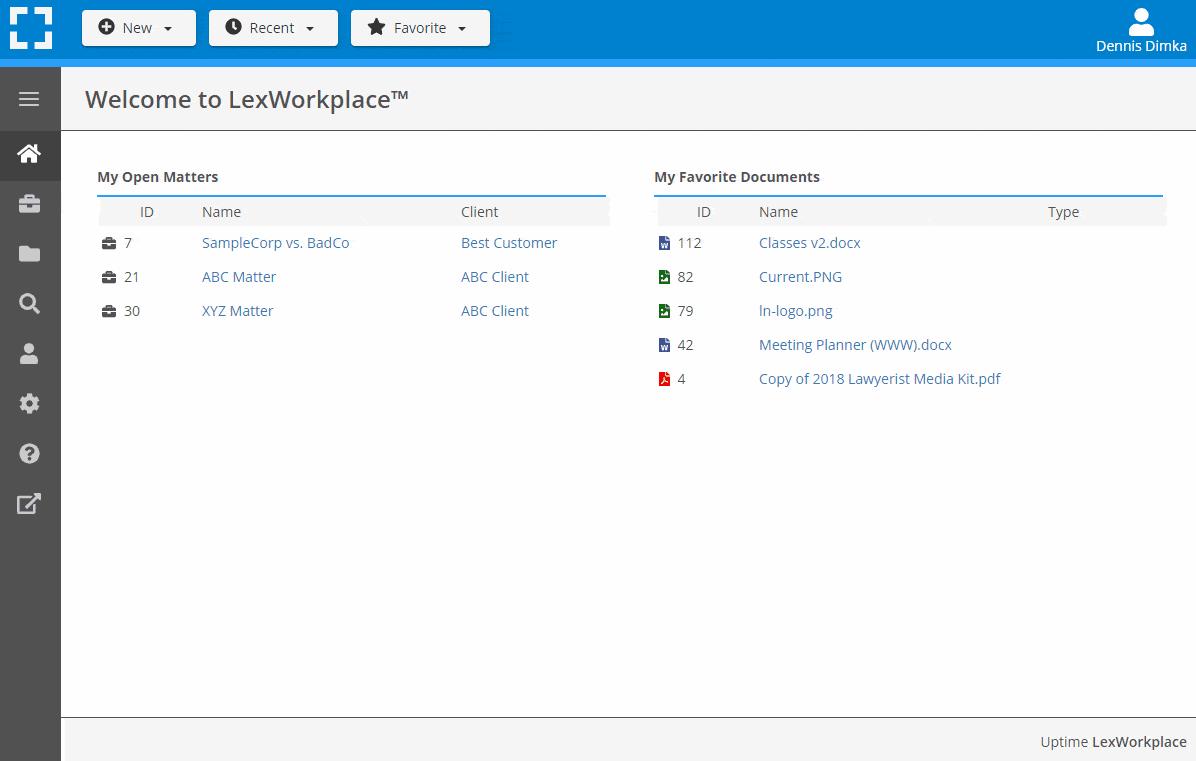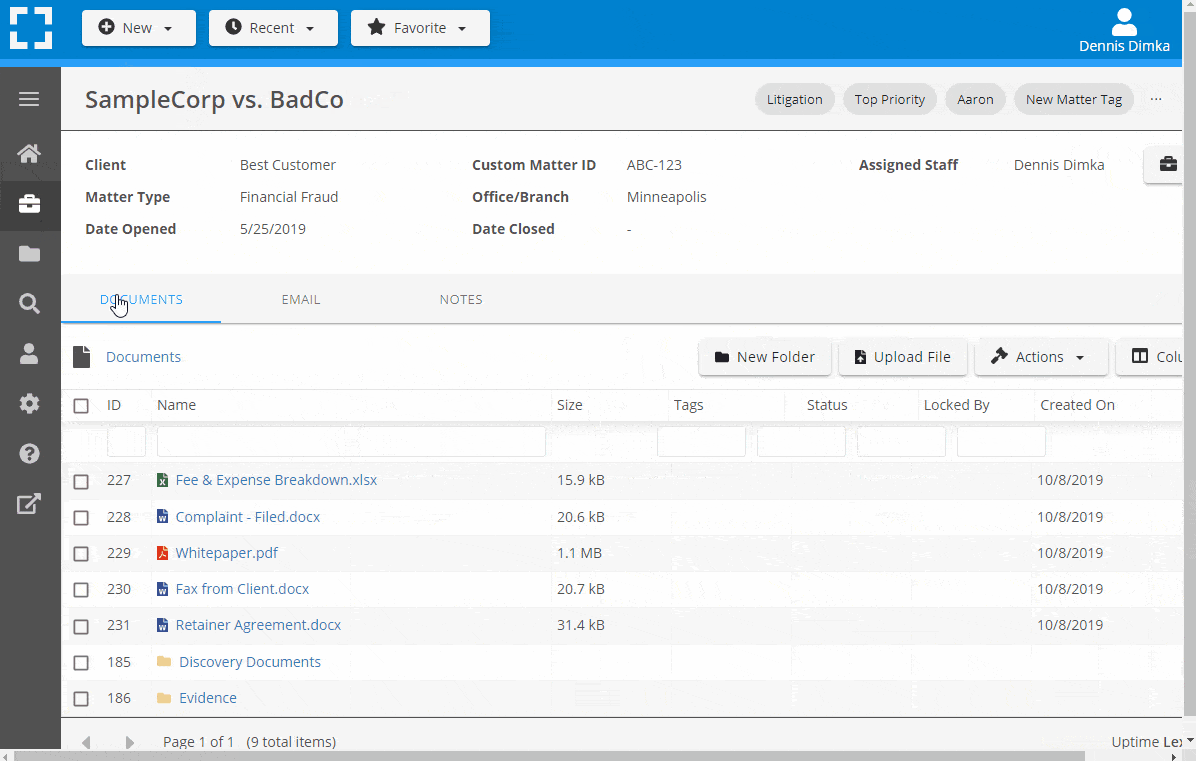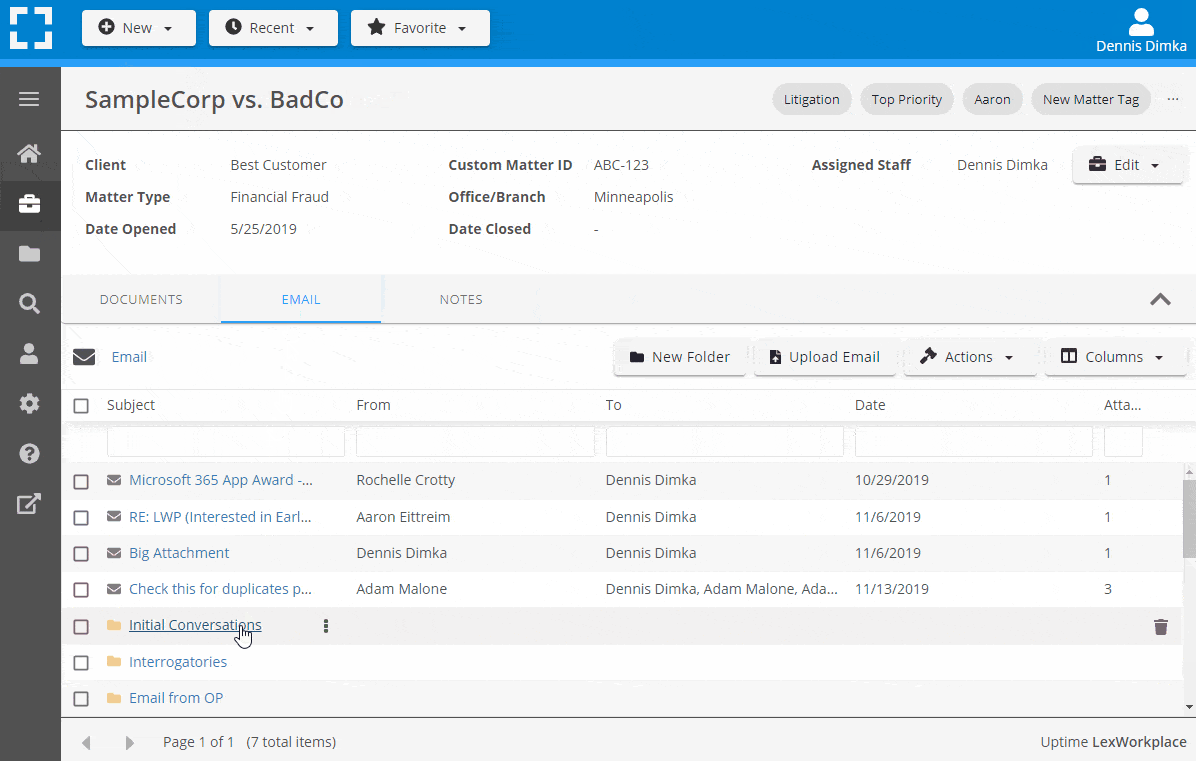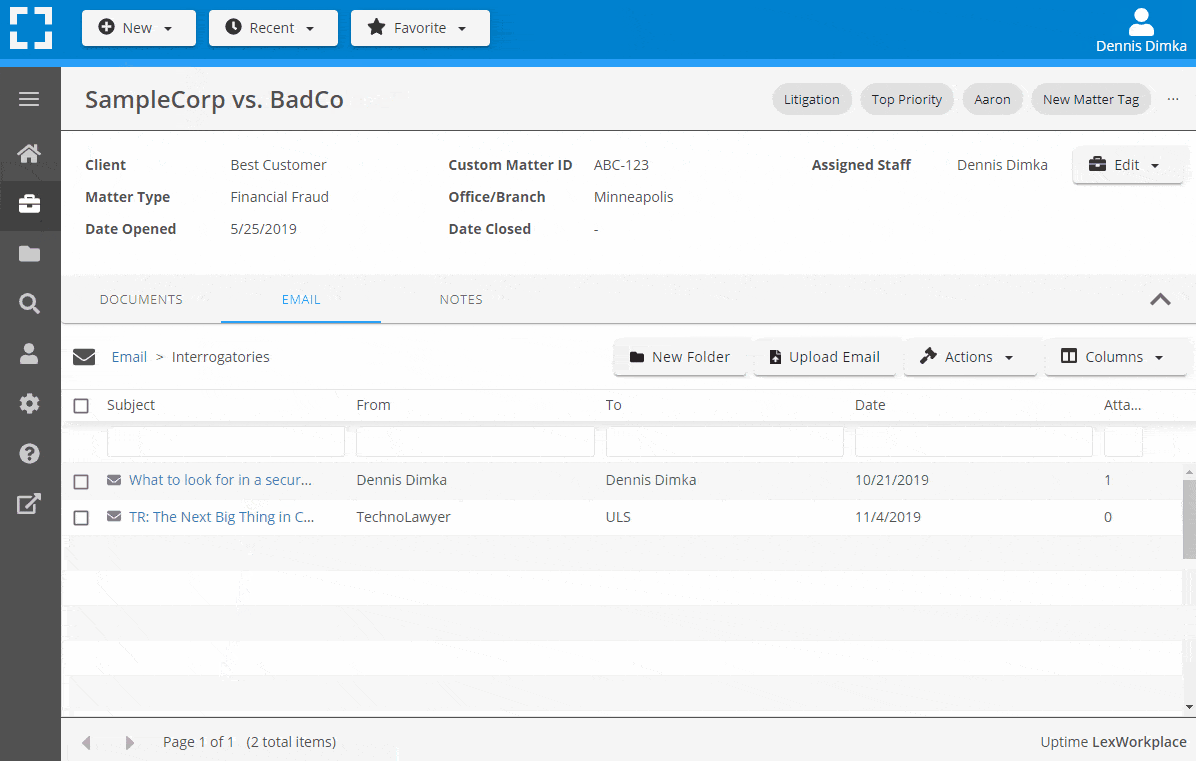
- Outlook Add-In that Works With Windows and Macs
- Save Entire, Original Email to a Matter in a LexWorkplace
- Email De-Duplication
- Organize Emails into Folders, Subfolders
Works with Windows and Macs
All of LexWorkplace is compatible with both Windows and Mac computers.
Next Steps
See What Clients Have to Say
Lawyers love LexWorkplace. See how the system streamlined one lawyer’s practice.
Watch the 5-Minute Demo
See LexWorkplace in action in our quick 5-minute overview and demonstration.
Or, if you want a one-on-one demo, or want to talk about LexWorkplace for your firm, schedule a call or demo below.
You Might Also Like
August 19, 2025
AI for Legal Documents: Top Tools Law Firms Use To Draft, Review, and Manage Faster
Struggling with slow legal document…
August 12, 2025
Why Law Firms Can’t Afford to Delay DMS Migration — And How to Switch Smoothly
Tired of costly, stressful tech…
June 23, 2025
Role-Specific Benefits of Document Management Software for Law Firms
Legal document management software…
Want More Legal Technology Tips?
Subscribe to Uptime Legal to get the latest legal tech tips and trends, delivered to your inbox weekly.


