Legal Document Management Security

This article delves into why robust security measures are no longer optional but essential for law firms. We mustn’t ignore increasing threats posed by cyber-attacks and data breaches, the unique challenges in safeguarding confidential legal documents, nor the critical consequences of neglecting these security aspects.
With a focus on comprehensive security features, including encryption, access control, and multi-factor authentication, we provide insights into best practices and emerging trends in secure document management.
Join us in exploring the pivotal role of document management security and the continuous journey towards achieving and maintaining impeccable data security standards in the legal industry.
Whether you’re adapting to a remote work model or enhancing your current security protocols, this piece serves as a vital guide to protecting your firm’s and clients’ sensitive information in the digital realm.
In This Article
- Introduction to Document Management Security
- Understanding Risks and Challenges
- Key Components of Document Management Security
- Best Practices for Document Management Security
- Managing Data Security in a Remote Work Environment
- Preparing for and Responding to Data Breaches
- Frequently Asked Questions — Document Management Security
Introduction to Document Management Security
In the realm of legal practice, the security of document management systems has transcended from a mere best practice to an indispensable element of operations.
The sanctity of client information and the integrity of legal processes hinge on how effectively a law firm manages and secures its documents.
Here, we lay the groundwork for understanding the critical importance of document management security in today’s digital-dominated legal landscape.
The Digitalization of Legal Documentation
The shift from paper-based to digital documentation has brought about immense benefits in terms of efficiency and accessibility.
However, this transformation also introduces new vulnerabilities.
Digital documents, if not adequately protected, are susceptible to cyber threats ranging from data breaches to unauthorized access, potentially leading to severe consequences for both clients and law firms.
The Role of Document Management Software in Ensuring Security
In this context, document management software, like LexWorkplace, plays a pivotal role.
By offering specialized security features tailored for legal document management, they provide the tools necessary to safeguard sensitive information against the evolving landscape of digital threats.
Encryption of documents, both in transit and at rest, robust access controls, secure sharing options, and geographic data redundancy are just a few examples of how a DMS may fortify a law firm’s security posture.
While you always retain some responsibility for cybersecurity, choosing a DMS that prioritizes data security relieves your law firm of significant burden.
LexWorkplace Top Features
Cloud-based Document Management
- Secure Cloud Storage
- Client/Matter-Centric Org
- Full-Text Document Search
- Secure Client Sharing
- MS Office Add-In
- Email Management
- Windows + Mac Compatible
As we delve deeper into this article, we will explore the various dimensions of document management security, the challenges and risks involved, and the best practices for ensuring the highest standards of data protection in the legal sector.
Let’s dive in!
Related – Best Legal Document Management Software: Evaluate various document management software to ensure your firm’s utilizing the best option.
Understanding Risks and Challenges
Recognizing and mitigating risks is a task of paramount importance.
This section delves into the common security threats faced by law firms and the unique challenges involved in protecting legal documents.
Common Data Security Threats
Law firms are increasingly targeted by a range of cyber threats, each with its unique implications:
Cyber-attacks
This broad category includes sophisticated ransomware attacks, where malware encrypts vital data, demanding a ransom for access.
Phishing scams, where employees are tricked into revealing sensitive information, are also prevalent.
Other forms of cyber-attacks include Distributed Denial of Service (DDoS) attacks, which can cripple a firm's operations, and Man-in-the-Middle (MitM) attacks, which intercept and potentially alter communications.
Data Breaches
These occur when unauthorized parties gain access to confidential information.
Causes range from hacking to internal vulnerabilities, such as weak passwords or unpatched software.
The implications of a data breach are far-reaching, potentially exposing client details, case strategies, and other sensitive data.
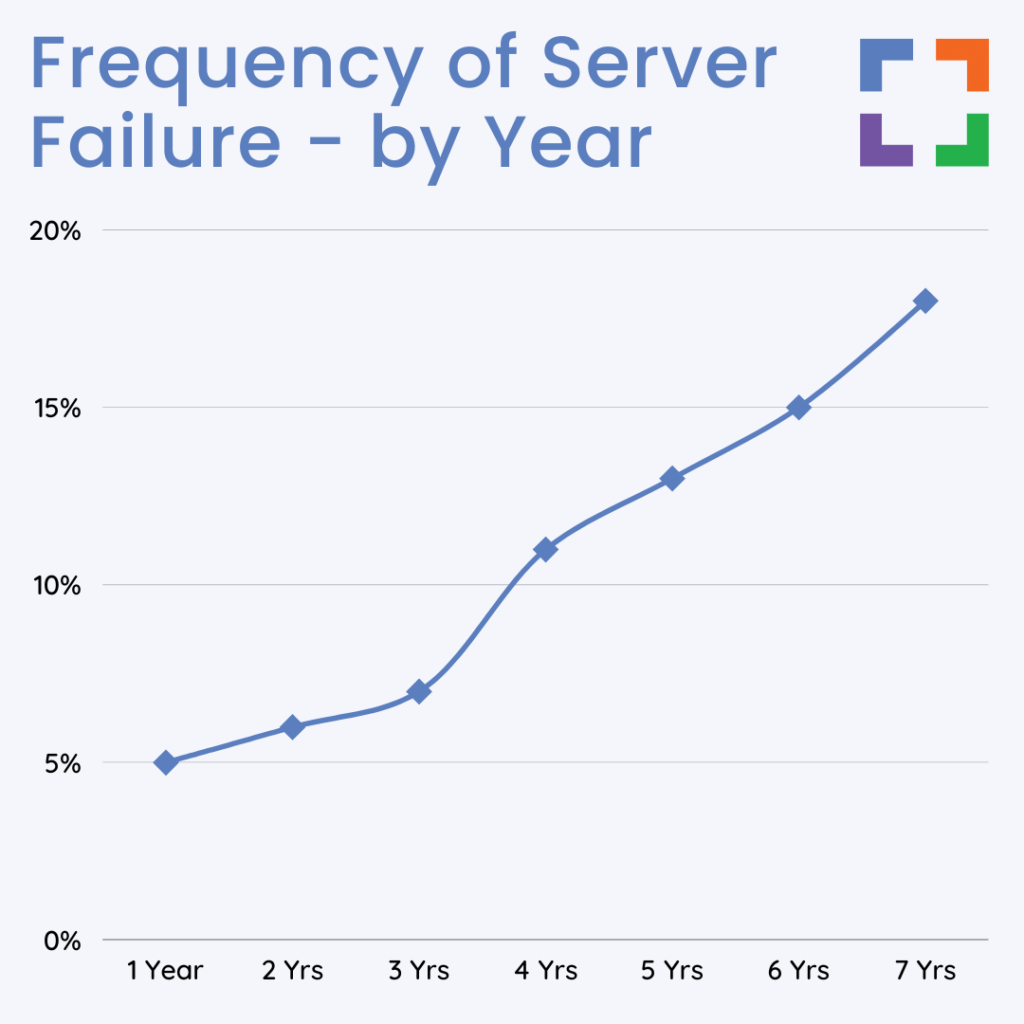
Server Failure
Server failure refers to the unexpected shutdown or malfunction of the servers that host and manage the law firm's data.
This can be due to hardware malfunctions, software issues, power outages, or natural disasters.
A server failure can lead to significant data loss or data inaccessibility, disrupting legal operations. For a law firm, this could mean the inability to access critical case documents, loss of client information, and interruption in legal proceedings.
Unique Challenges in Securing Legal Documents
The legal sector faces specific challenges in document security due to the nature of its work:
Confidentiality Obligations
Lawyers are bound by attorney-client privilege, requiring them to maintain the confidentiality of client information.
This legal obligation adds a layer of complexity to how documents are managed, stored, and shared.
Client Privacy Concerns
Clients share sensitive information with their legal representatives, often pertaining to personal or business matters.
This makes it imperative for law firms to employ a security framework that upholds the highest standards of privacy.
Complex Regulatory Landscape
Law firms must navigate a myriad of regulations, including GDPR, HIPAA (for healthcare-related cases), and various state-level data protection laws.
Non-compliance not only risks legal penalties but also the firm’s license to practice.
The Consequences of Inadequate Data Security
The repercussions of neglecting document management security are significant and multifaceted:
Legal Repercussions
Data breaches can lead to lawsuits and regulatory actions against a law firm.
Non-compliance with data protection laws like GDPR can result in hefty fines, legal sanctions, and in severe cases, disbarment.
Reputational Damage
A firm’s reputation is its most valuable asset. A breach can erode client trust, affecting both current and potential client relationships.
Restoring a tarnished reputation is often a long and challenging process.
Financial Losses
The financial impact extends beyond direct losses from a breach.
It encompasses the cost of forensic investigations, increased insurance premiums, loss of business, and expenses associated with legal defense and settlement.
LexWorkplace Success Story
See how one law firm uses LexWorkplace to organize their documents and streamline their practice.
Book a 15-Minute Demo
Understanding and addressing these risks and challenges is a critical task for any law firm.
This deep dive into the nature of threats and the complexity of document security in legal practice underscores the importance of adopting a rigorous and well-rounded approach to protecting sensitive information.
In the following sections, we will explore how DMS solutions, like LexWorkplace, are specifically designed to meet these challenges, ensuring the security and integrity of legal documentation in an increasingly digital and interconnected world.
Key Components of Document Management Security
Legal document management security involves several crucial components, each playing a pivotal role in safeguarding sensitive information.
In this section, we focus on the key security features your chosen DMS ought to have, illustrating how they should address the unique needs of legal document management.
LexWorkplace, for example, provides all of the security features discussed below. Learn more here.
Encryption - Ensuring Data Confidentiality
At Rest and In Transit: Encryption is vital for protecting documents.
Encrypting data at rest (when stored) and in transit (when being sent or received) prevents unauthorized access and interception. This dual encryption is crucial for law firms handling sensitive information.
Access Control - Managing Document Accessibility
Permission-Based Access: Effective document management security requires strict access control measures.
By implementing permission-based access, law firms can ensure that only authorized personnel have access to specific documents. This minimizes the risk of internal breaches and unauthorized sharing.
Secure Document Sharing - Maintaining Integrity in Collaboration
Encrypted Sharing Mechanisms: Sharing legal documents with external parties necessitates secure sharing capabilities.
Implementing encrypted sharing methods protects the documents from being compromised, maintaining their integrity even outside the firm's internal network.
Counteracting Email Vulnerabilities: Recognize the limitations and security risks of standard email communications.
Secure document sharing tools provide a safer alternative for exchanging sensitive information.
Geographic Data Redundancy - Preparing for the Unexpected
Backup and Recovery: To mitigate risks such as data loss or system failures, geographic data redundancy is crucial.
Storing data backups in multiple, geographically diverse locations ensures that information can be recovered and accessed even in the event of a regional disaster.
Multi-Factor Authentication (MFA) - Reinforcing User Verification
Enhanced Security Protocol: Implementing MFA adds an additional layer of security.
By requiring multiple forms of verification, law firms significantly reduce the likelihood of unauthorized system access, an important step in protecting against data breaches.
LexWorkplace Security
Cloud-based Document Management
- 256-bit Military-Grade Encryption
- Data Encryption In-Transit
- Data Encryption At-Rest
- Geographic Redundancy
- Multi-Factor Authentication
- Permissions
- Groups
Incorporating these key components into a legal document management system is essential for any law firm aiming to maintain the highest standards of data security.
They form a comprehensive approach to protecting sensitive legal documents from the growing range of digital threats in today’s interconnected world.
This framework not only safeguards client information but also upholds the firm’s reputation and compliance with regulatory requirements.
Best Practices for Document Management Security
To ensure the utmost security in legal document management, law firms must adhere to a set of best practices.
These practices not only protect sensitive client data but also help in maintaining compliance with various regulatory standards.
Here, we outline the key strategies that can significantly enhance the security of legal document management systems.
Consistent Security Policy Enforcement
- Implementation: Create a detailed security policy that covers every aspect of document handling, from creation to archiving and disposal. This policy should include guidelines on document access, sharing, and storage.
- Benefit: A unified policy ensures that all staff members are on the same page, reducing inconsistencies and gaps in security practices. It also serves as a reference point for addressing security incidents.
Regular Software and System Audits
- Implementation: Regularly schedule audits to assess the security of document management systems. These audits should identify vulnerabilities, outdated software, and potential areas for improvement.
- Benefit: Routine audits help in early detection of security flaws, ensuring that the systems are fortified against emerging threats and conform to the latest security standards.
Advanced Data Encryption Strategies
- Implementation: Employing advanced encryption techniques, such as end-to-end encryption, can significantly enhance the security of documents, especially during transmission.
- Benefit: Advanced encryption ensures that data is unreadable to unauthorized individuals, providing a strong barrier against interception and unauthorized access.
Continuous Staff Training and Sensitization
- Implementation: Implement a continuous training regime that includes updates on the latest cyber threats, best practices in cybersecurity, and legal requirements regarding data protection.
- Benefit: A well-informed staff is the first line of defense against cyber threats. Continuous training fosters a security-conscious culture within the firm, reducing the likelihood of human error leading to security breaches.
Comprehensive Incident Response Planning
- Implementation: Develop a detailed incident response plan outlining immediate actions, communication protocols, and recovery steps in case of a security breach.
- Benefit: An effective response plan minimizes the impact of a breach, helps in rapid recovery, and ensures transparent communication with stakeholders, thereby preserving the firm's reputation.
Stringent Control Over External Collaboration
- Implementation: Implement strict protocols for sharing documents with external parties, including authenticated access and detailed logging of all external interactions with documents.
- Benefit: This control minimizes the risks associated with external collaborations, ensuring that document integrity and confidentiality are maintained even outside the firm's internal network.
Embracing Advanced Methods
- Implementation: Keep abreast of technological advancements like AI for threat detection or managed IT services for handing off technology, and integrate these technologies where beneficial.
- Benefit: Leveraging cutting-edge technologies can provide law firms with advanced tools for detecting and preventing security threats, as well as enhancing the overall integrity and traceability of document management processes.
Practice Foundation
Practice Next
FULL PRIVATE CLOUD
All of your software, documents and data in secure Private Cloud. Work in a flexible virtual desktop environment.
LEGAL TECH SUITE
Practice Next is a suite of Managed IT, Legal Software Support, and Cloud Essentials, made exclusively for law firms.
By thoroughly implementing these best practices, law firms can significantly bolster their document management security.
This proactive and comprehensive approach is key to protecting sensitive client information and maintaining the firm’s reputation in an increasingly digital and interconnected legal landscape.
Managing Data Security in a Remote Work Environment
The shift towards remote work presents unique challenges and opportunities in the realm of legal document management security.
Law firms must adapt their strategies to secure sensitive information while accommodating flexible, remote work arrangements. This section explores the best practices for managing data security in a remote work environment.
Secure Connection Protocols
Implementing robust, encrypted connection protocols is fundamental.
Virtual Private Networks (VPNs) and Remote Desktop Protocols (RDPs) are essential tools. VPNs safeguard data transmission to and from the firm's network, while RDPs provide secure access to office desktop environments, ensuring a consistent and secure workspace.
Endpoint Security
Endpoint security is paramount in remote work settings.
This involves comprehensive device management policies, mandating antivirus software, firewalls, and regular security updates.
For employees using personal devices, Bring Your Own Device (BYOD) policies need to outline security measures, including secure containers or virtualization to separate work and personal data.
Cloud-Based Security
Utilizing encrypted cloud storage solutions for data storage and access is vital.
Integrating Data Loss Prevention (DLP) tools within cloud services ensures that sensitive information is monitored and protected, mitigating the risk of data breaches.
Remote Work Policies and Physical Security
Developing clear remote work policies is crucial, including guidelines for data handling, secure file sharing, and communication protocols.
Physical security measures should also be addressed, providing guidance on the secure storage and disposal of sensitive printed materials.
Training and Network Security
Regular training sessions on security best practices and potential threats are essential in building a culture of security awareness.
Additionally, guidelines for securing home Wi-Fi networks and policies regarding the use of public networks help strengthen network security at remote locations.
Authentication and Testing
Extending two-factor or multi-factor authentication to all access points, including email and cloud services, adds an extra layer of security.
Regular penetration testing and vulnerability assessments can identify and rectify weaknesses in the remote work infrastructure.
Incident Management and Collaboration Tool Security
Tailoring incident response protocols for remote scenarios ensures preparedness for any security breaches.
Ensuring the security of all communication and collaboration tools used by remote teams is also critical.
Contractor and Compliance Management
Implementing strict security measures for contractors and third-party vendors who access the firm’s data ensures that external entities adhere to the firm’s security standards.
Compliance with legal and regulatory standards like GDPR and HIPAA must also be maintained.
Mental Health and Well-Being
Recognizing the impact of remote work on mental health and promoting a healthy work-life balance can indirectly contribute to security.
This approach reduces the likelihood of errors or oversights due to stress or burnout.
By adopting this multi-faceted strategy, law firms can effectively manage the risks associated with remote document handling, maintaining the high standards of confidentiality and integrity crucial to the legal profession.
This comprehensive approach blends technology, policy, and employee awareness, forming a robust shield around sensitive data in any remote work scenario.
Another way to approach cybersecurity in a remote environment is by handing off your IT needs to a service provider, such as Uptime Practice.
Related – Law Firms and Cloud Security: Data is priceless, and you have an obligation to protect it. Learn more.
Preparing for and Responding to Data Breaches
Where data breaches are increasingly common, law firms must be prepared to respond effectively.
This preparation not only minimizes potential damage but also ensures compliance with legal obligations and maintains client trust.
The following outlines a strategic approach to preparing for and responding to data breaches in the legal sector.
1
Developing an Effective Incident Response Plan
- Incident Response Team: Establish a dedicated team responsible for managing data breaches. This team should include members from IT, legal, compliance, and communications departments.
- Clear Procedures: Develop clear, step-by-step procedures for the team to follow in the event of a breach. This includes identifying the breach, containing it, eradicating the cause, and recovering any lost data.
- Regular Updates and Training: The incident response plan should be regularly updated to reflect new threats and solutions. Regular training sessions for the response team and staff are crucial to ensure everyone understands their role in a breach scenario.
2
Immediate Actions in the Event of a Data Breach
- Detection and Identification: Quickly identifying and confirming a breach is critical. This involves monitoring systems for unusual activity and having mechanisms in place to detect breaches promptly.
- Containment: Once a breach is detected, immediate steps should be taken to contain it. This may involve disconnecting affected systems, revoking access rights, or other measures to prevent further unauthorized access.
- Assessment and Investigation: Assess the scope and impact of the breach. Determine what data was accessed or stolen, and identify the cause of the breach to prevent future occurrences.
3
Legal Obligations and Client Communication
- Compliance with Laws and Regulations: Understand and comply with all legal and regulatory requirements related to data breaches. This includes reporting the breach to relevant authorities and affected clients in a timely manner.
- Transparent Communication: Communicate with clients and stakeholders openly and honestly about the breach. Provide details about what happened, what data was affected, how you are responding, and what steps are being taken to prevent future breaches.
- Ongoing Support and Remediation: Offer support to clients affected by the breach, such as credit monitoring services, and take remedial actions to restore any lost data or services.
4
Post-Incident Analysis and Improvement
- Thorough Investigation: After managing the immediate aftermath of the breach, conduct a thorough investigation to understand how and why it happened. This should involve a complete audit of your systems and security measures.
- Implementing Improvements: Based on the investigation findings, implement necessary improvements to prevent similar incidents. This could involve updating security protocols, enhancing staff training, or upgrading technology.
- Documenting Lessons Learned: Keep a record of the breach, the response, and the outcomes. This documentation can be invaluable for future training and improving the incident response plan.
Preparing for and effectively responding to data breaches requires a proactive and comprehensive approach.
By having a robust incident response plan, understanding legal obligations, maintaining transparent communication, and continually learning and improving from each incident, law firms can navigate the complexities of data breaches while upholding their duty to protect sensitive client information.
Related – Cybersecurity for Law Firms: Want to learn more about cybersecurity? Check out this article to round out your perspective.
Frequently Asked Questions — Document Management Security
Document management security involves strategies and technologies to protect digital documents from unauthorized access, breaches, and other cyber threats, especially in a legal context.
Law firms handle sensitive client information; hence, document management security is vital to protect client confidentiality, maintain legal compliance, and uphold the firm’s reputation.
Common threats include cyber-attacks like phishing and ransomware, unauthorized access, data breaches, and accidental leaks due to poor handling or inadequate security measures.
Encryption converts documents into a code to prevent unauthorized access. It ensures that even if data is intercepted, it remains unreadable and secure.
Access control ensures that only authorized individuals can view, edit, or share specific documents, thus minimizing the risk of internal breaches and unauthorized sharing.
MFA is a security process that requires users to provide two or more verification factors to access a system. It adds an extra layer of security, protecting against compromised credentials.
Remote work introduces challenges like securing remote networks, managing device security, and ensuring secure access. Firms need robust policies and technologies to address these issues.
An effective response plan should include immediate actions for breach containment, communication strategies, legal compliance steps, and procedures for post-incident analysis and improvement.
Yes, with proper security measures like strong encryption, access controls, and regular security audits, cloud storage can be a secure option for managing legal documents.
Firms should regularly train staff, stay informed about the latest cybersecurity trends, conduct routine security audits, and consult with cybersecurity experts to ensure their practices are up-to-date.
Looking for Document Management Software?
LexWorkplace:
Modern Document Management for Law Firms
LexWorkplace is document & email management software, born in the cloud and built for law firms. Here’s a quick primer on how it works.
Organize by Client & Matter
Organize documents, email and notes by client or matter. Store and manage all data for a case or project in one place.
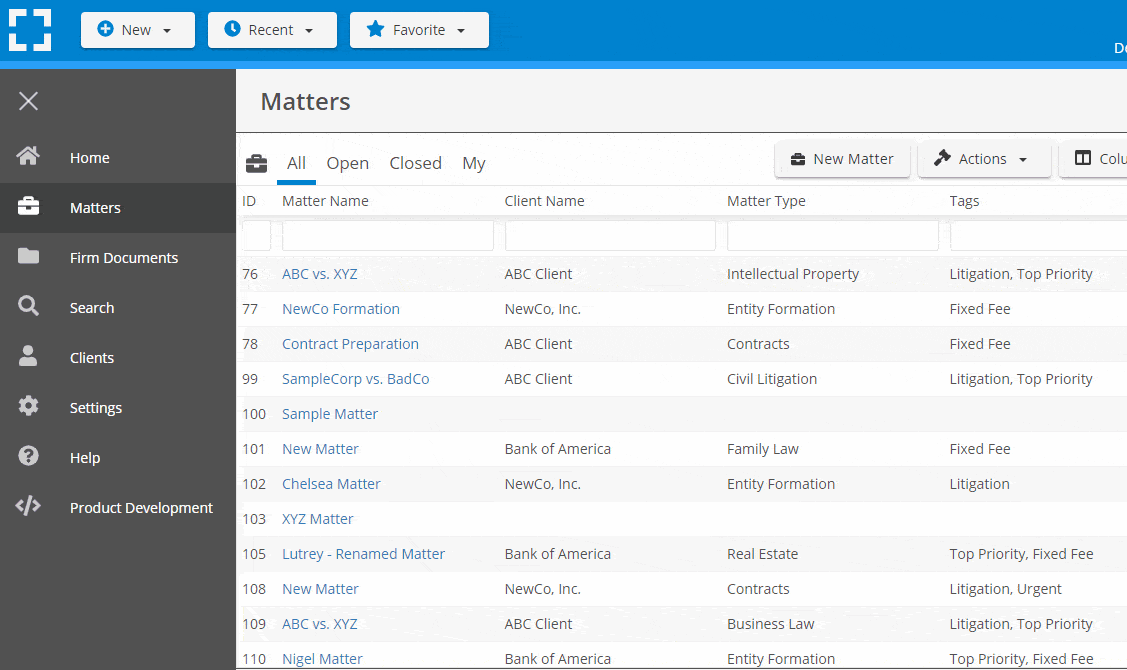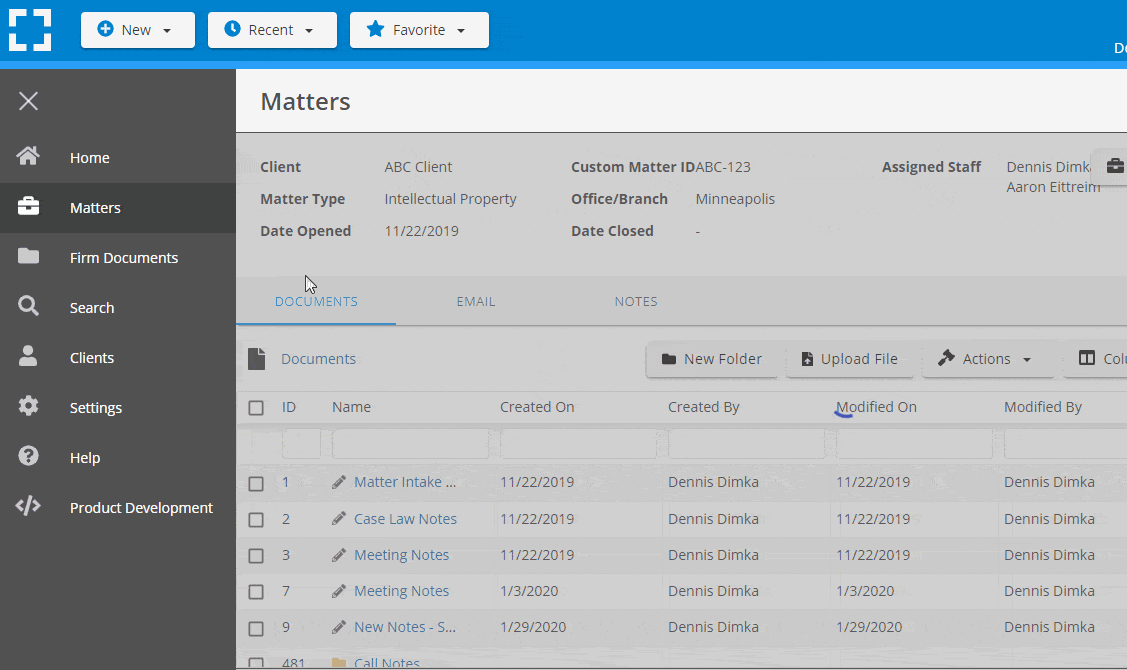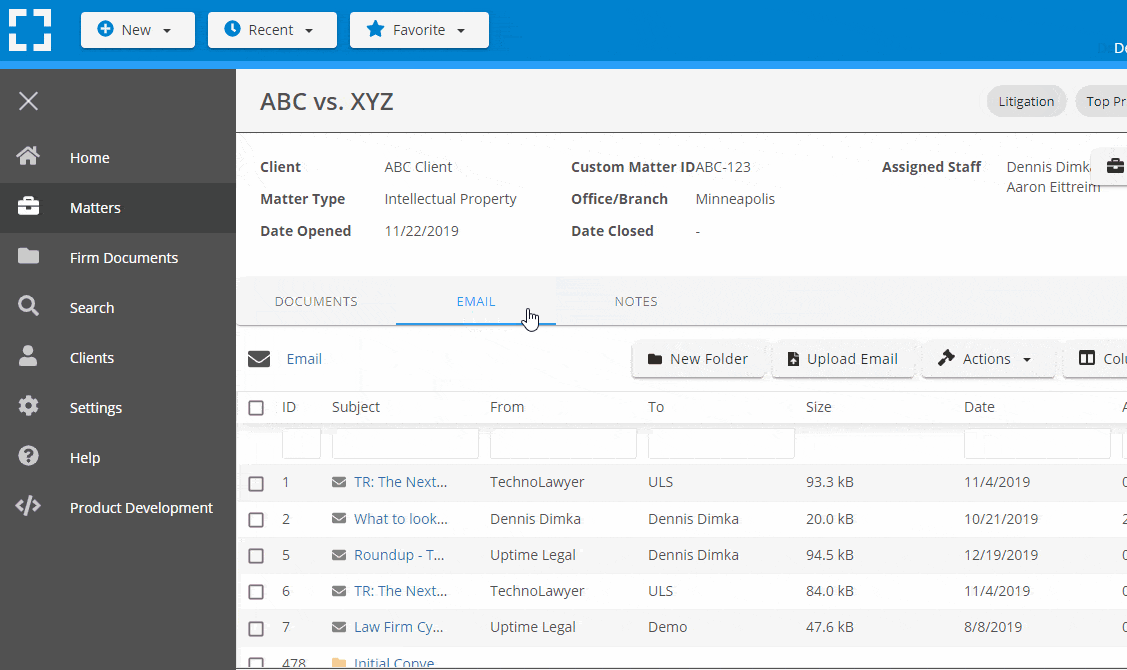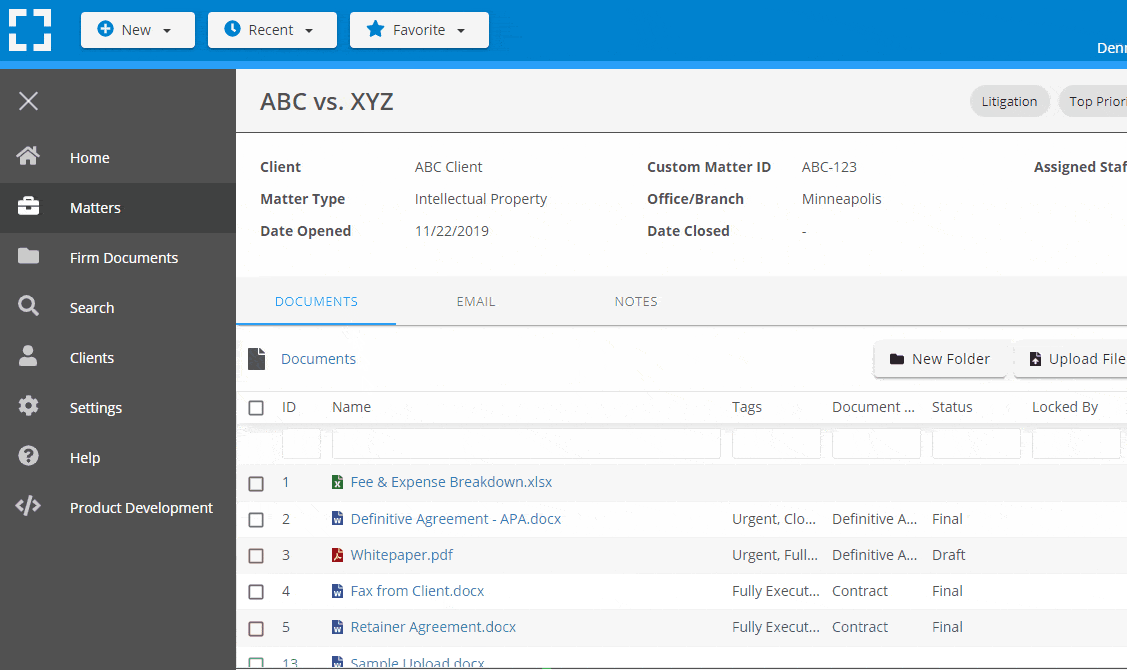
Go Beyond Basic Files & Folders
Supercharge your firm’s productivity with true DMS functions.
- Version Management
- Document Tagging & Profiling
- Document Check-Out / Check-In
- Microsoft Office Integration
- Automatic, Integrated OCR
- Convert Word Docs to PDF
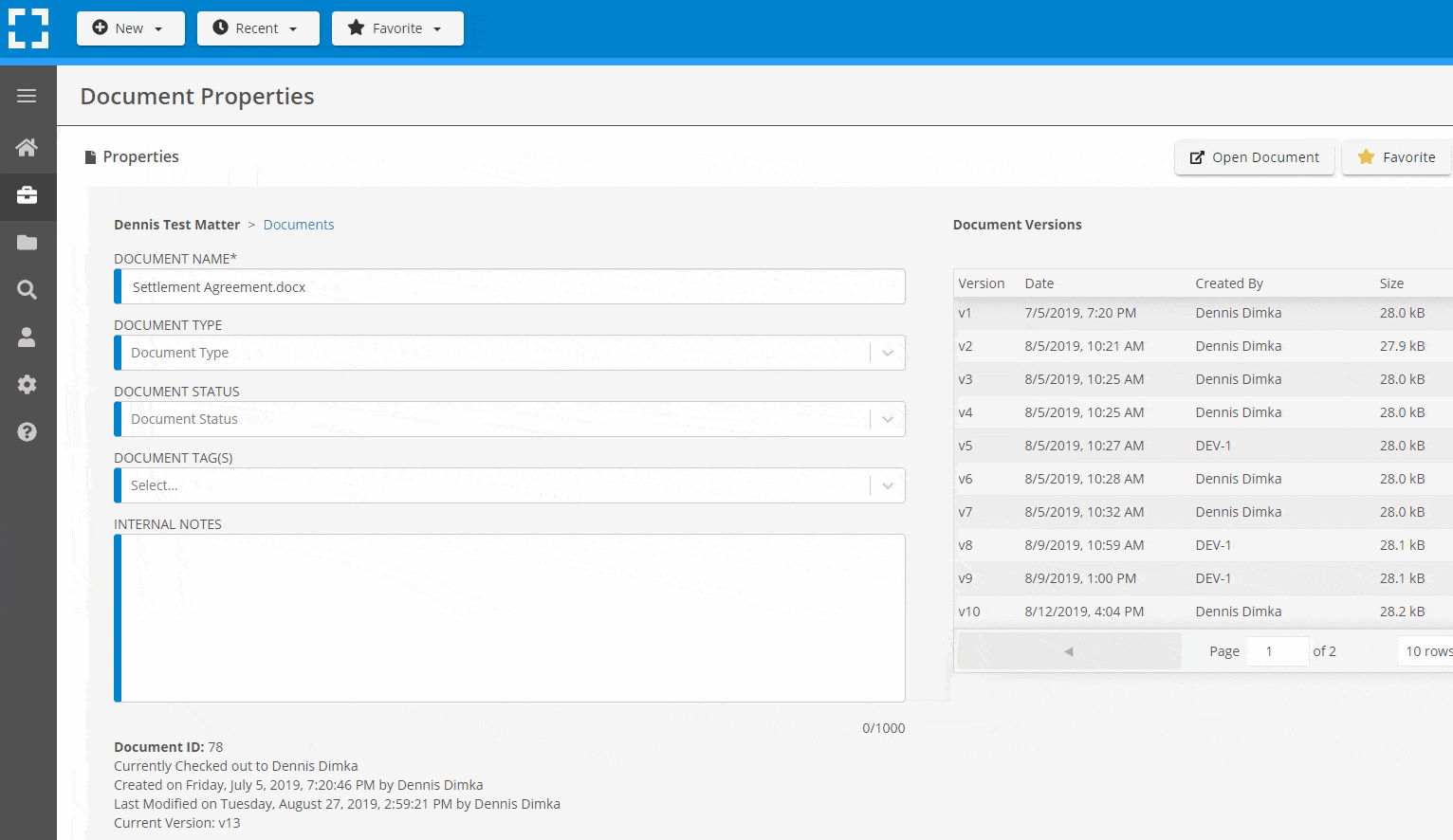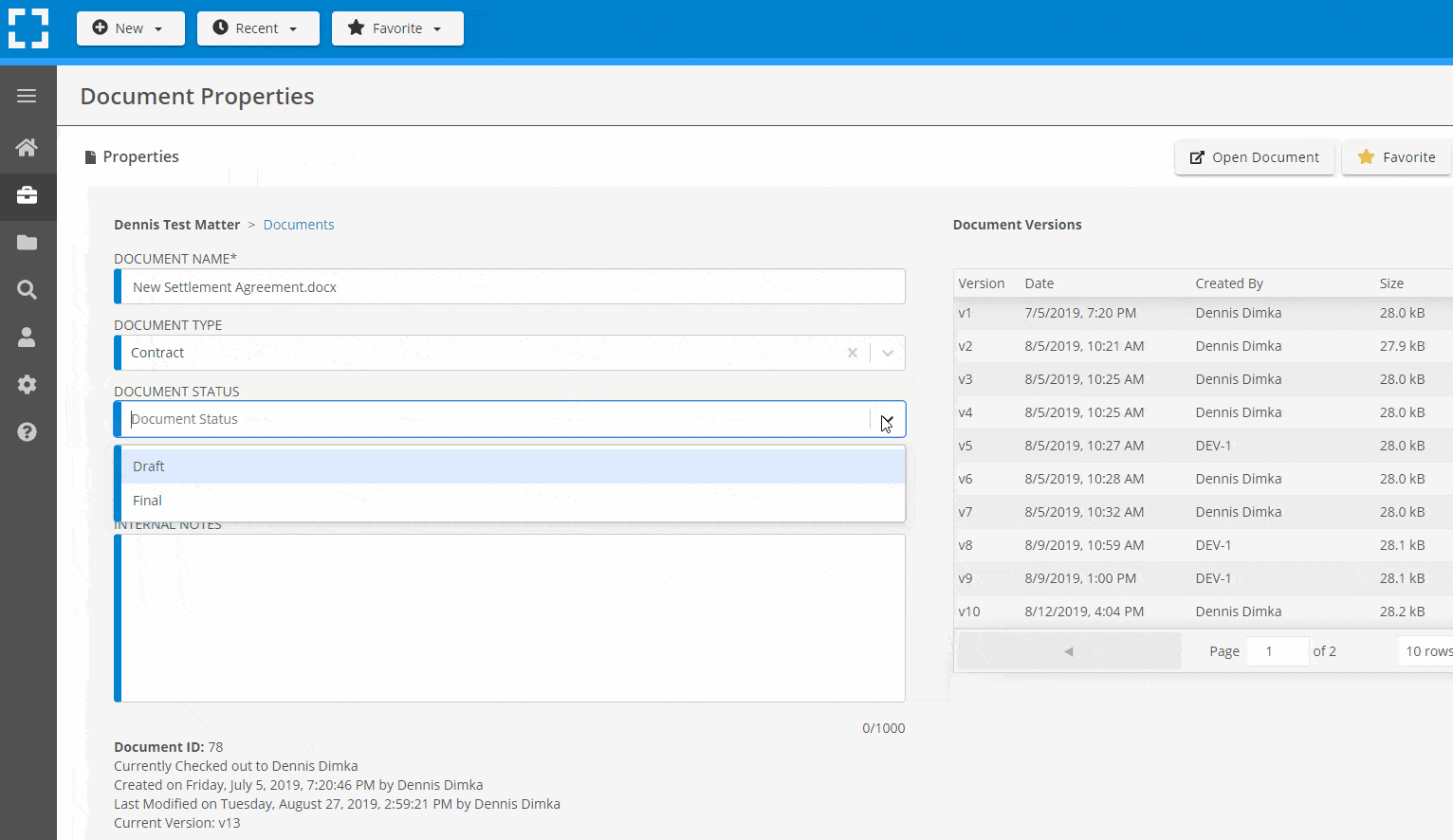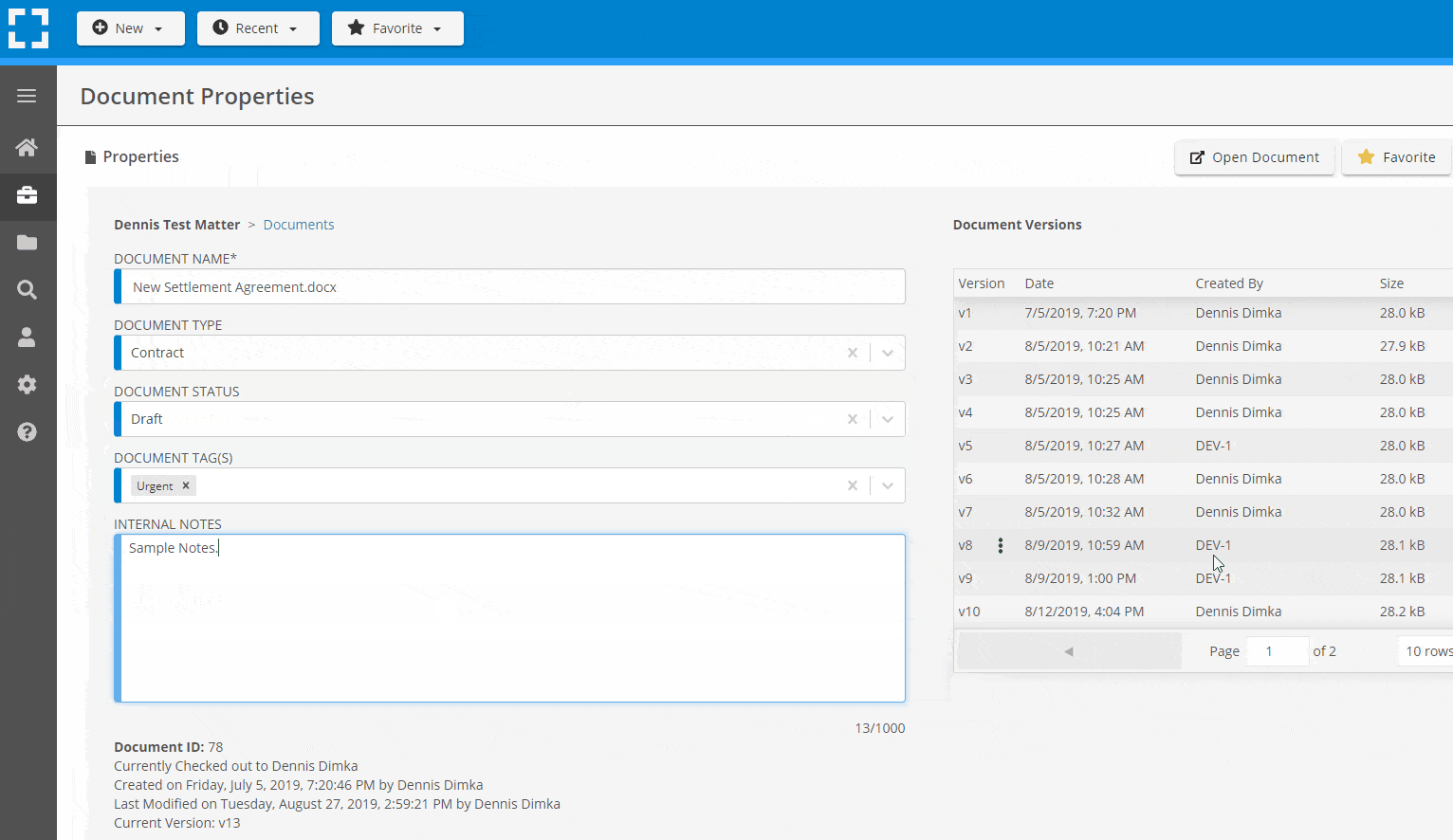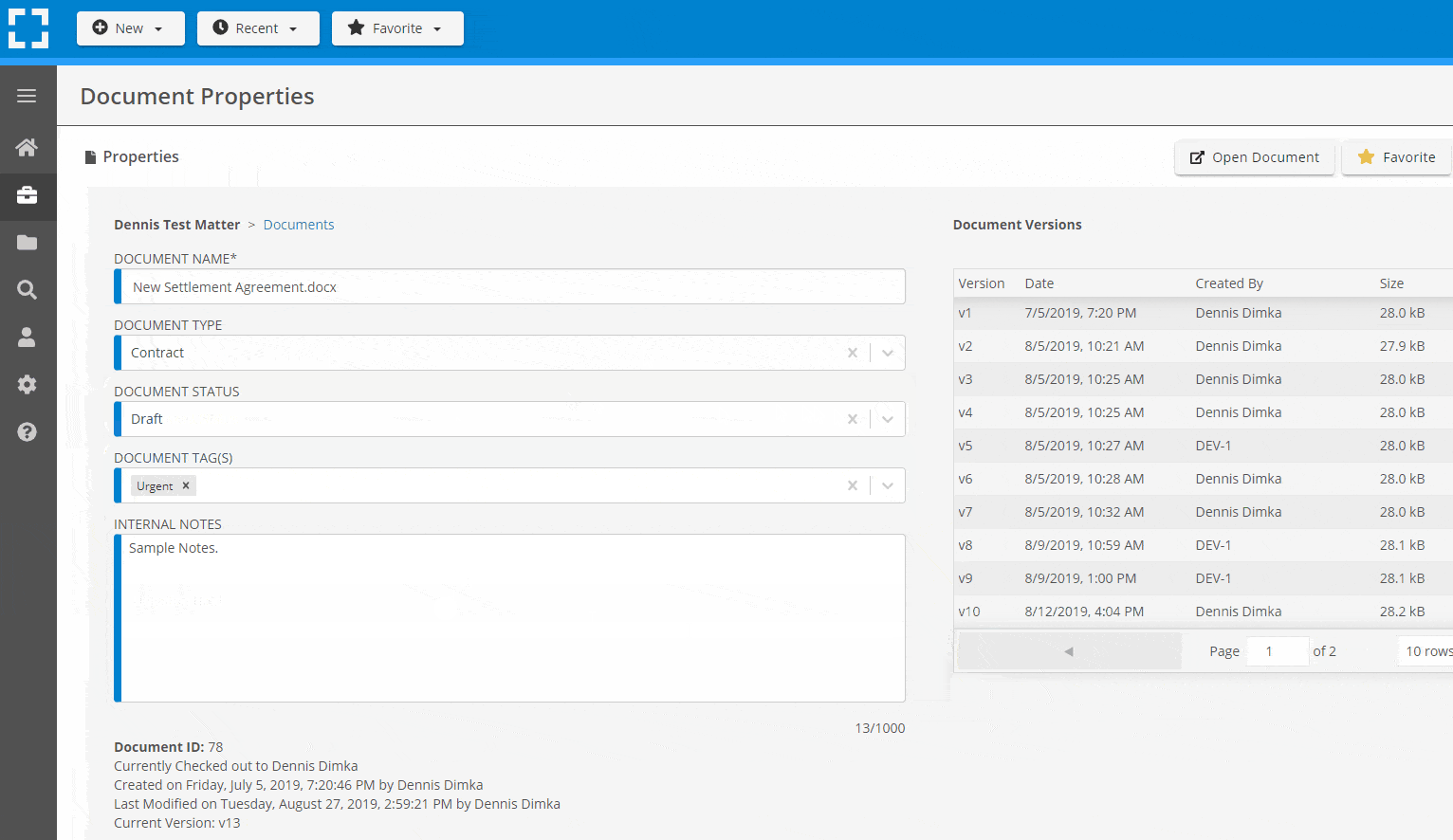
Search Everything
LexWorkplace is like Google for your law firm. Search across millions of pages, documents, folder email and notes in seconds. Refine your search by matter, document type, author and more.
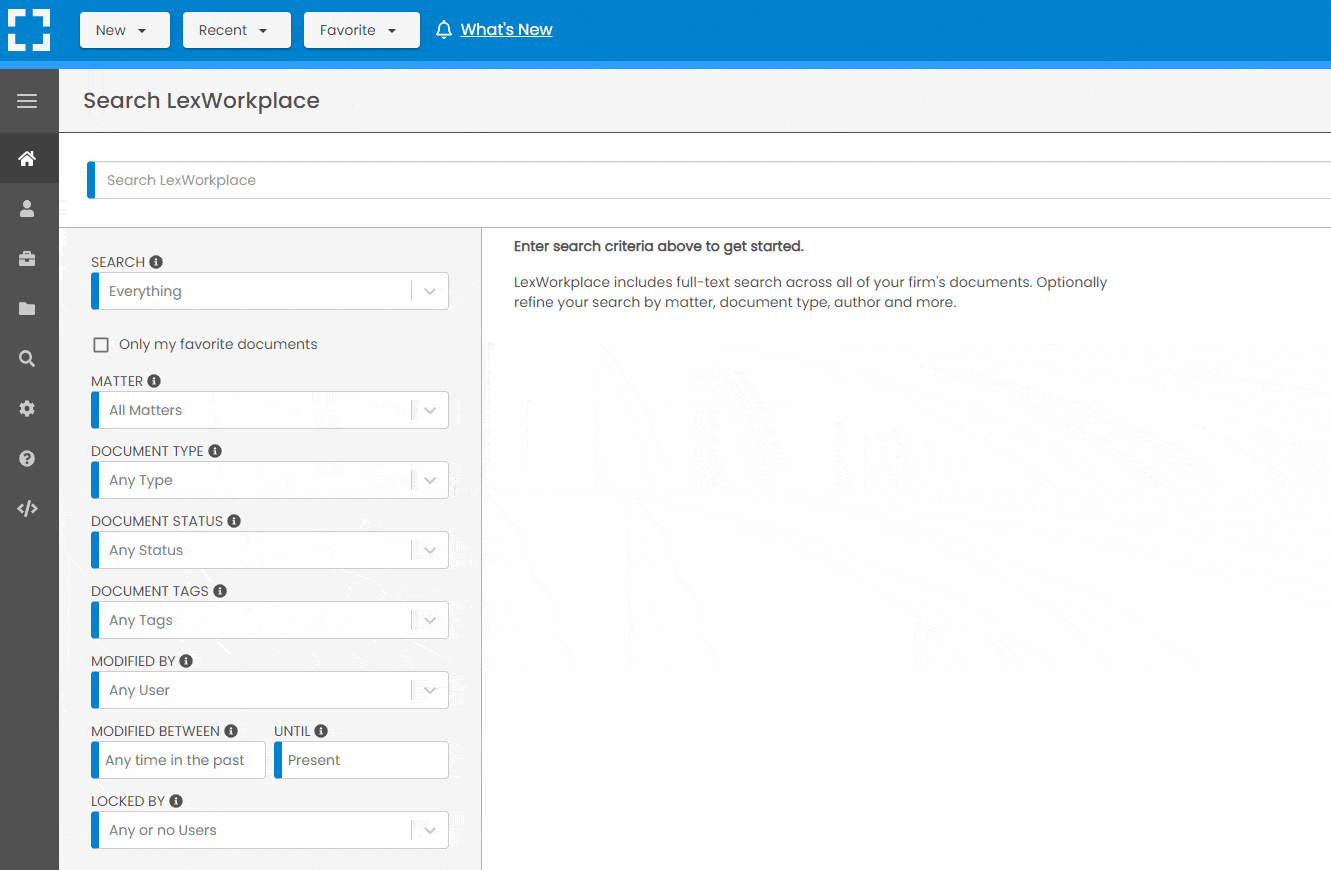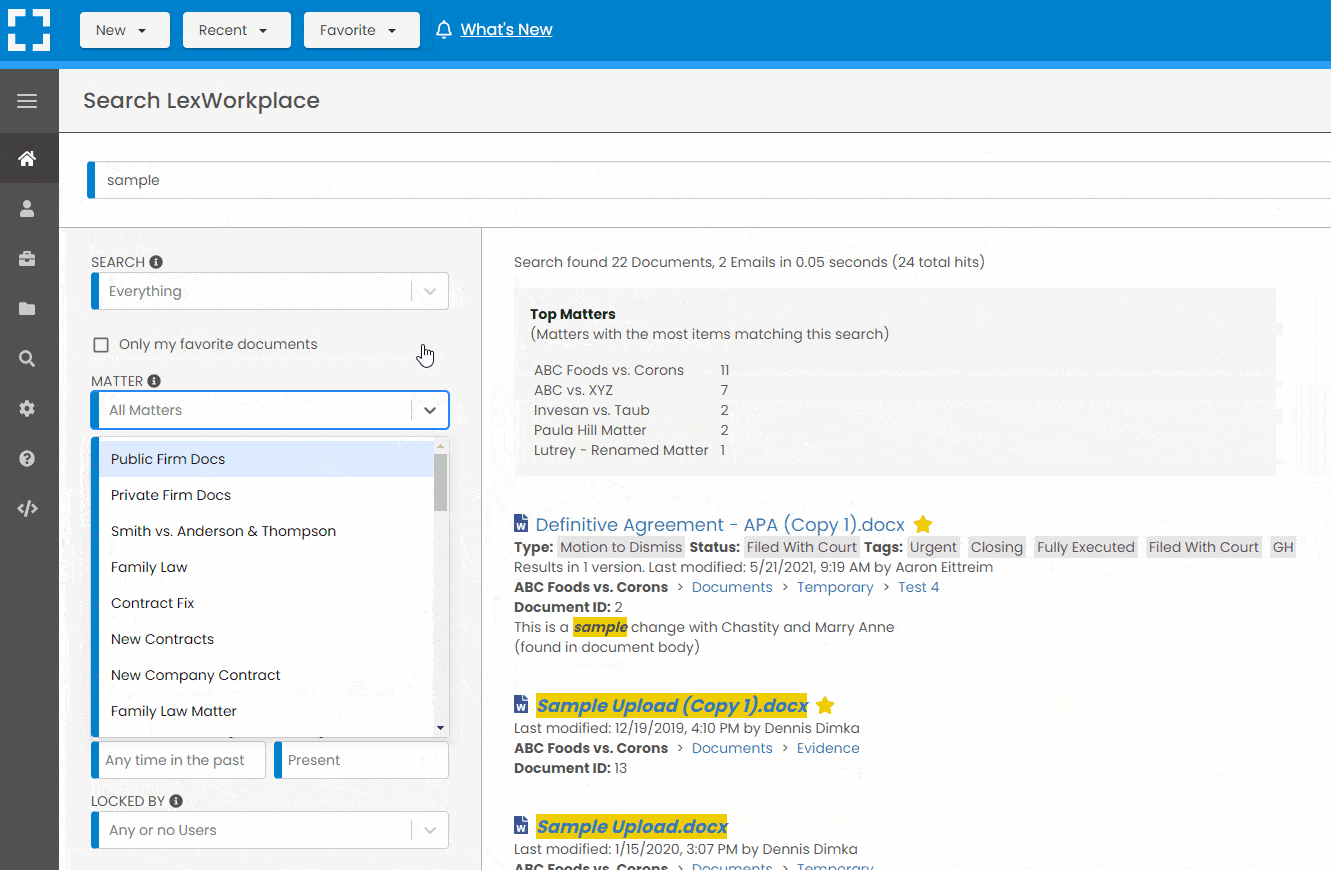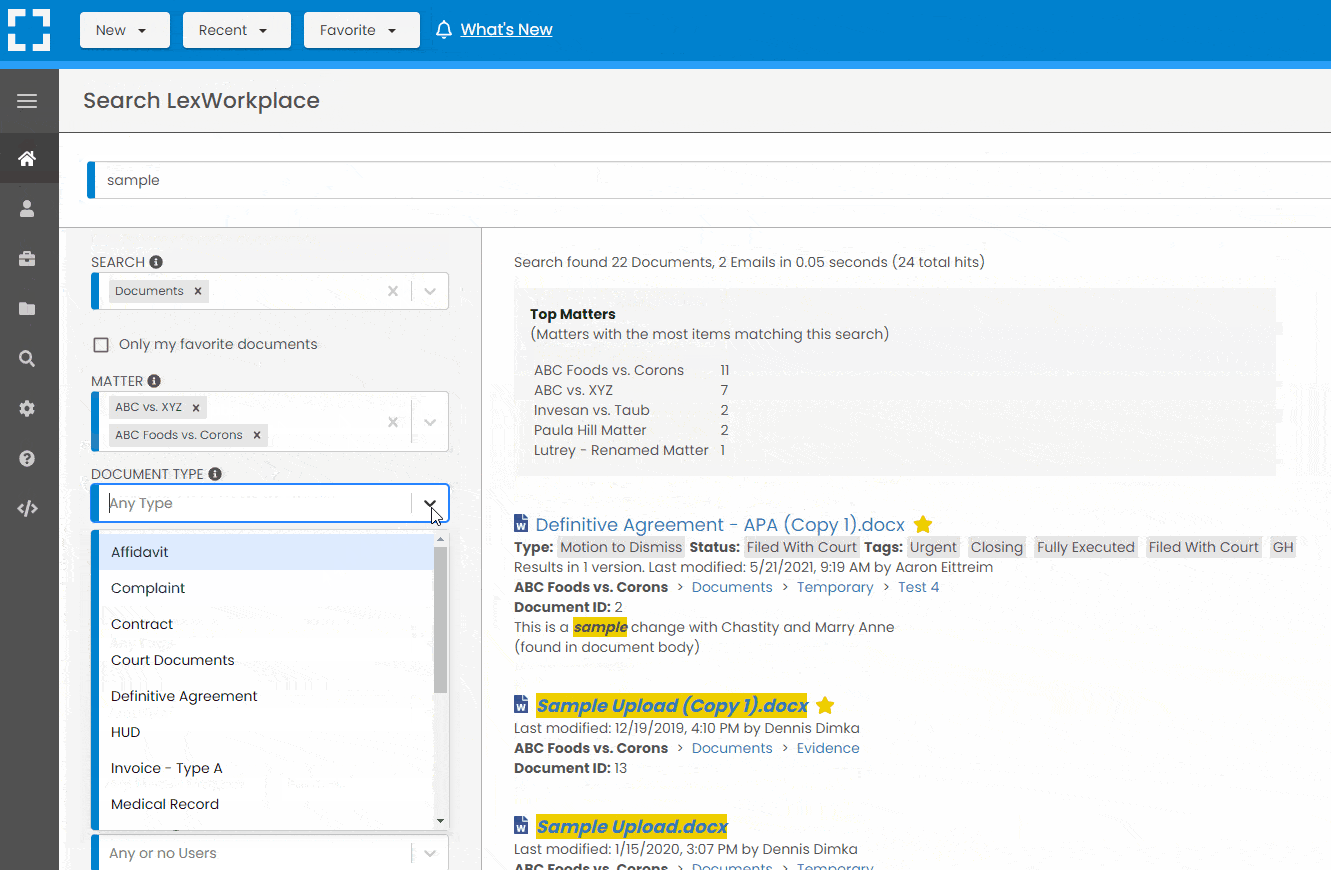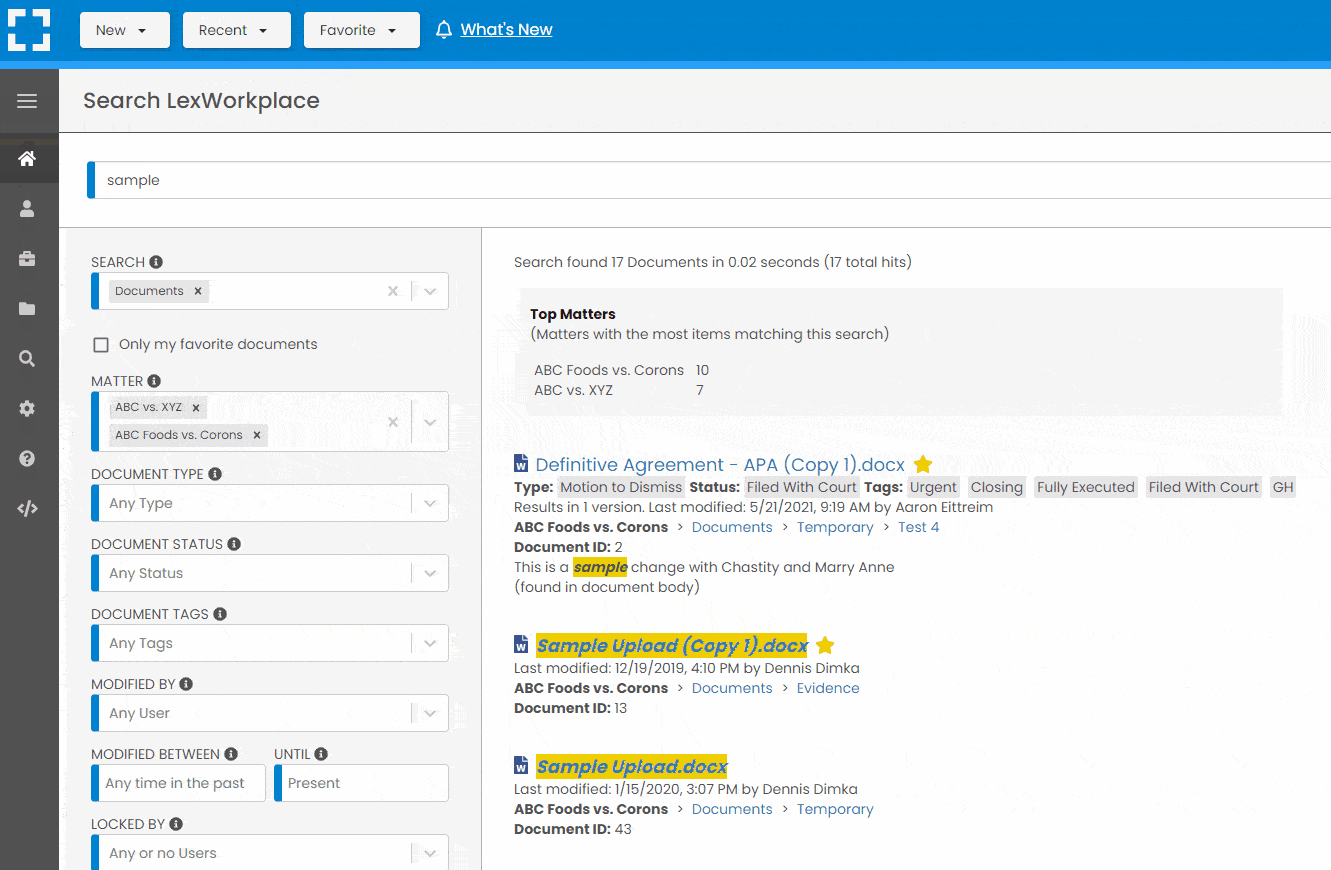
Search by…
- Client or Matter
- Document Type (Contract, Complaint, Order, etc.)
- Document Status (Draft, Final, etc.)
- Document Tags (Filed With Court, Fully Executed, etc.)
Outlook Integration + Comprehensive Email Management
Save emails to a matter without leaving Outlook. Saved emails are accessible to your entire team, organized and searchable.
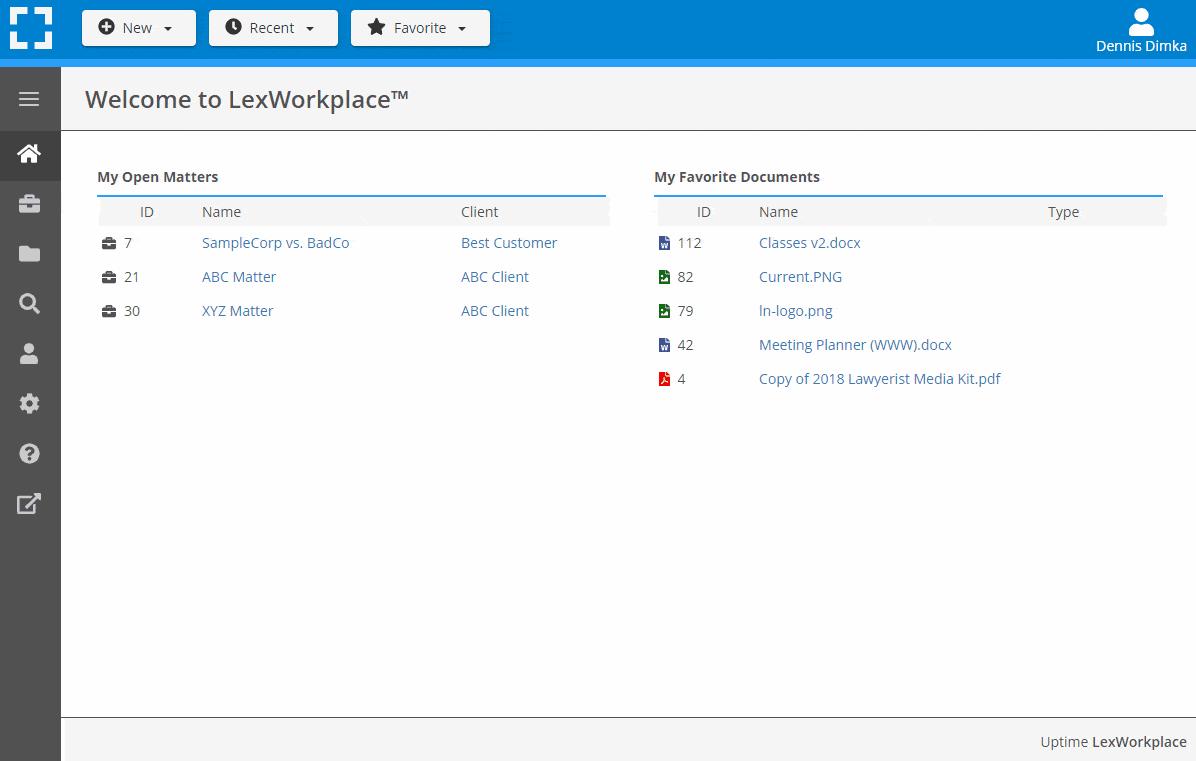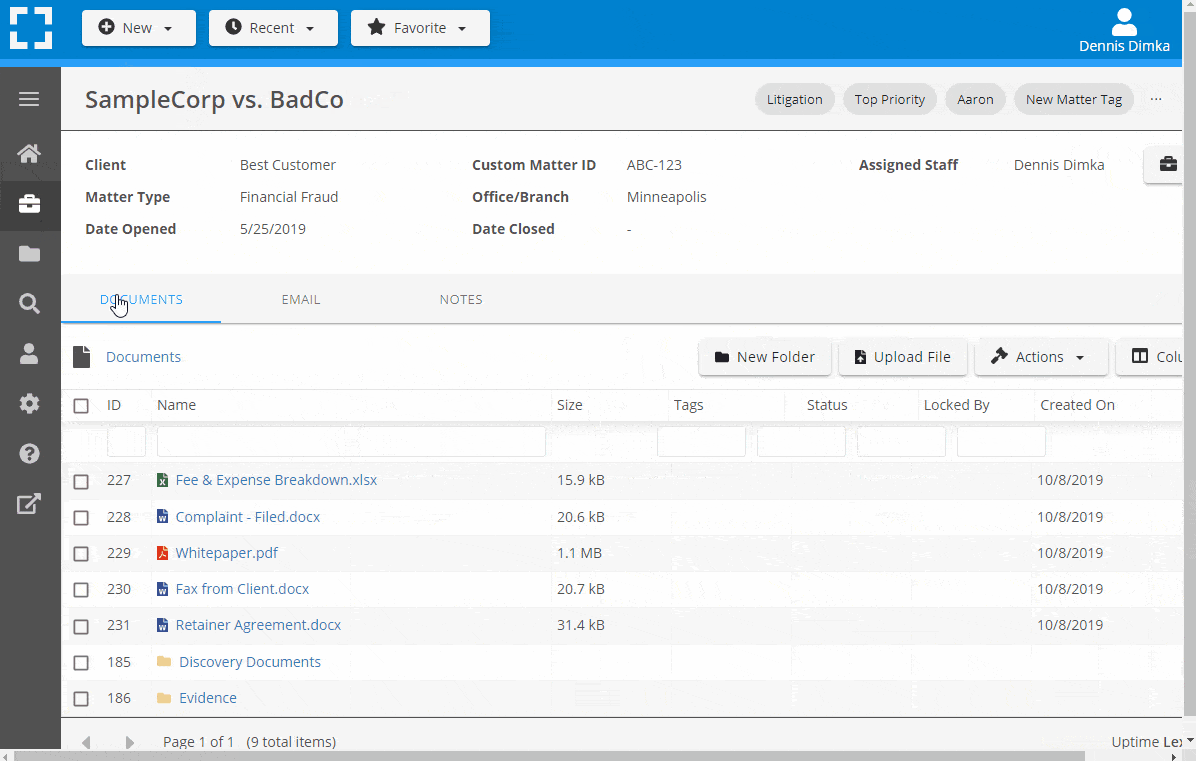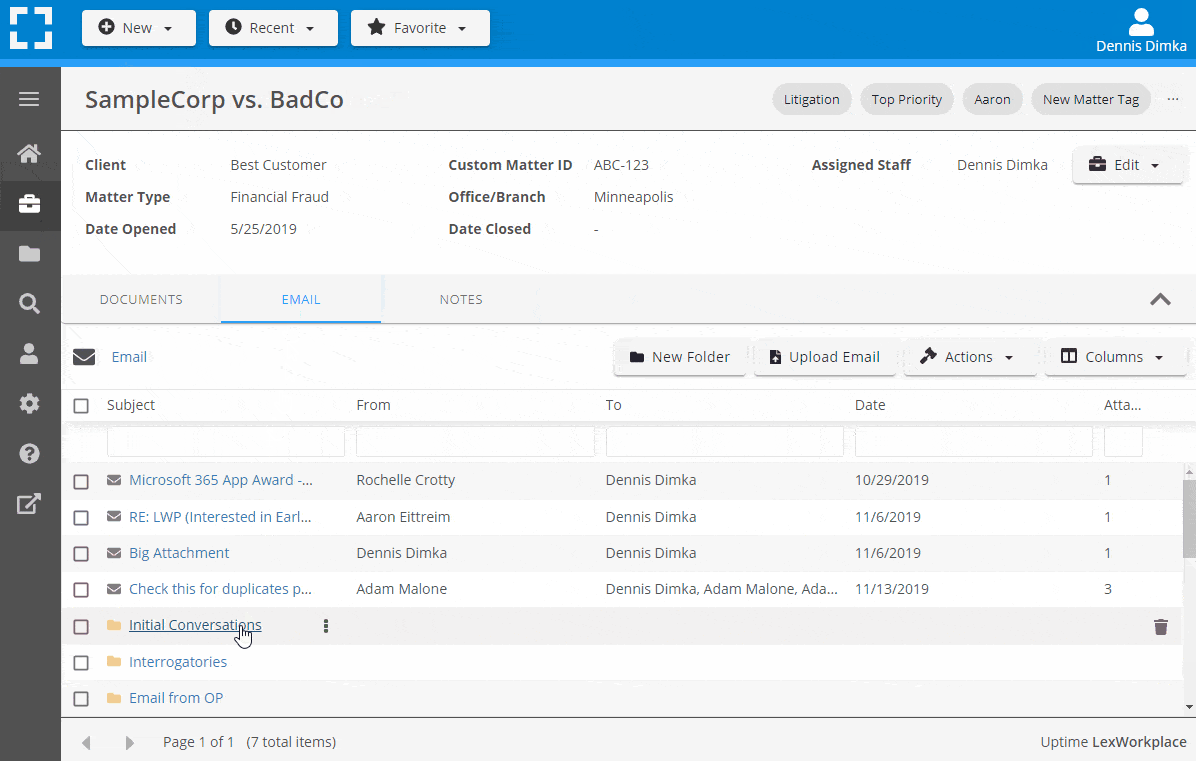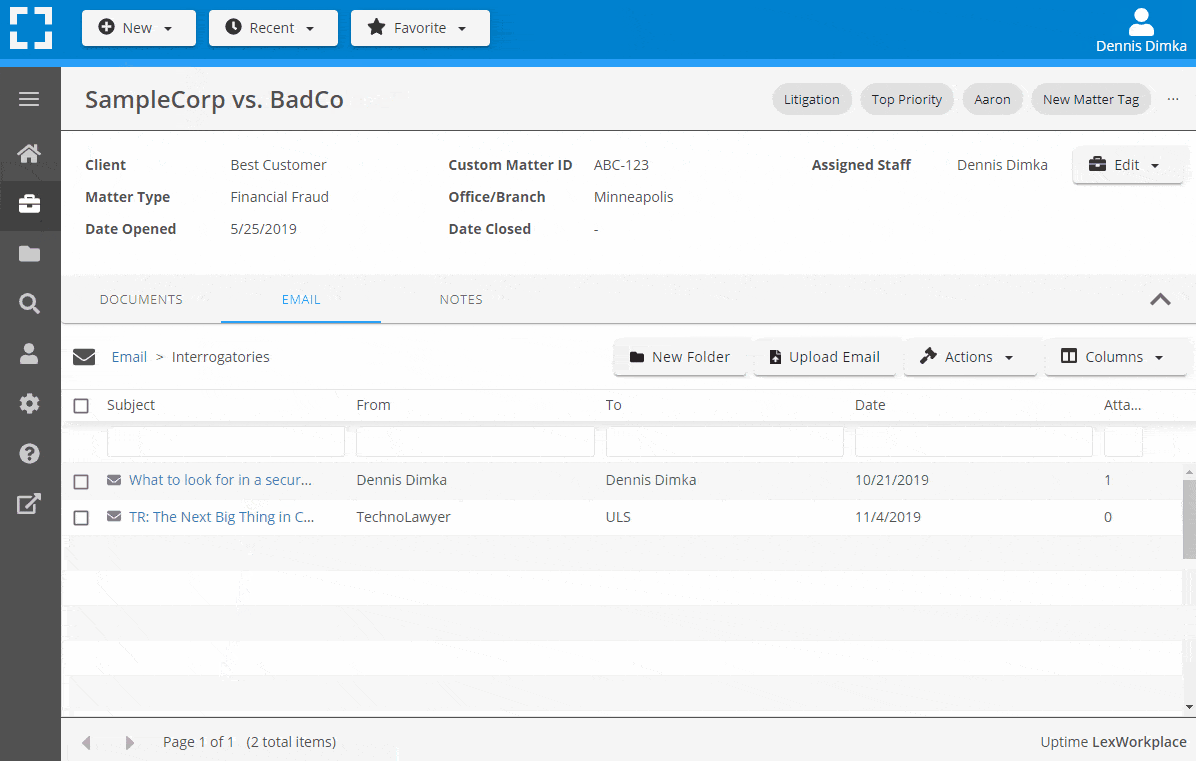
- Outlook Add-In that Works With Windows and Macs
- Save Entire, Original Email to a Matter in a LexWorkplace
- Email De-Duplication
- Organize Emails into Folders, Subfolders
Works with Windows and Macs
All of LexWorkplace is compatible with both Windows and Mac computers.
What Clients Say
Lawyers love LexWorkplace. See how the system streamlined one lawyer’s practice.
Watch the 5-Minute Demo
See LexWorkplace in action in our quick 5-minute overview and demonstration.
Or, if you want a one-on-one demo, or want to talk about LexWorkplace for your firm, schedule a call or demo below.
You Might Also Like
April 12, 2024
AI for Legal Documents: Benefits, Use Cases, and AI Tools
Discover how AI is changing legal…
March 28, 2024
Law Firm Software: Your 2024 Guide to Building Your Tech Stack
Top Law Firm Software: Practice…
Want More Legal Technology Tips?
Subscribe to Uptime Legal to get the latest legal tech tips and trends, delivered to your inbox weekly.